Step-by-Step Guide to Implementing Microsoft Defender for Office 365 and Phishing Simulations


In today’s digital world, organizations face increasingly sophisticated email-based attacks, including phishing, malware, and ransomware. Email is one of the most targeted attack vectors, making it critical to have robust security solutions to protect sensitive information and maintain organizational integrity. At Medha Cloud, we assist organizations by leveraging Microsoft Defender for Office 365, a cloud-based security platform that mitigates these risks by providing advanced protection for email and collaboration tools.
In this report, I will demonstrate how we configured Microsoft Defender for Office 365 to protect an organization against email-based threats, phishing, malware, and other malicious attacks.
Project Overview
A medium-sized company with 500 employees, including remote workers has experienced an increase in phishing attempts and email-based threats, prompting the IT team to implement a robust security solution. The goal is to protect email accounts, raise employee awareness through phishing simulations, and implement a reporting mechanism for suspicious emails.
Project Objectives:
- Implement Microsoft Defender for Office 365 to protect against email threats such as phishing, malware, and malicious links.
- Run phishing simulations to assess employee awareness and provide training.
- Create a reporting mechanism so employees can report suspicious emails directly from Outlook.
Implementation Based on the Project Objectives
Microsoft Defender for Office 365 Deployment
We begin by configuring Microsoft Defender for Office 365 to shield the organization from email-based threats, and below are the step-by-step configurations.
Step 1: Configure Anti-Phishing Policies
The company had experienced impersonation attacks targeting high-level staff and users associated with the company domain name. The Medha Cloud Security and Compliance team implemented an anti-phishing policy to protect executives (e.g., CEO, CFO) and the company domain name from impersonation.
To accomplish this, we followed these steps:
- Logged in to the Microsoft Defender portal in the company's M365 tenant.
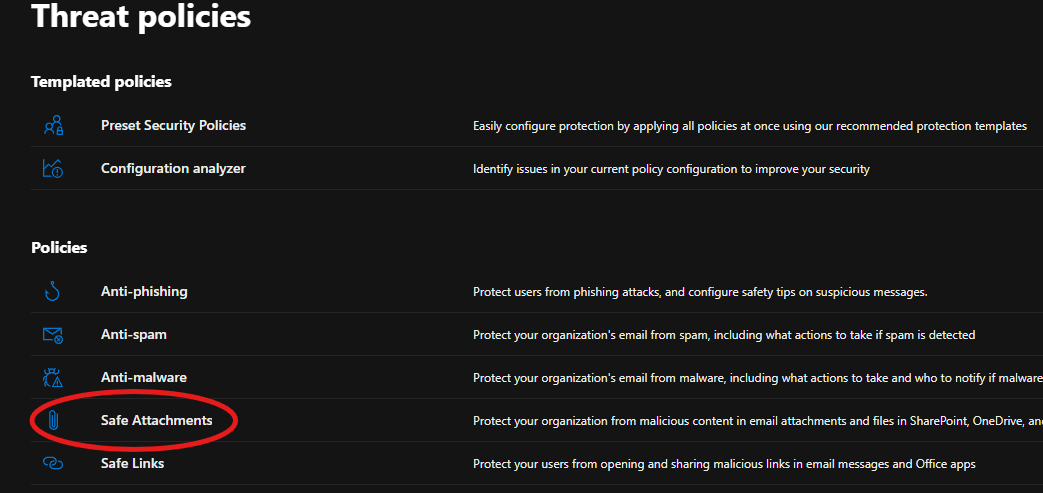
- Navigated to Email & Collaboration, selected Policy & Rules, clicked on Threat Policies, and then accessed Anti-phishing to create a targeted anti-phishing policy for executives and high-level employees.
The attached screenshot illustrates the configuration process.
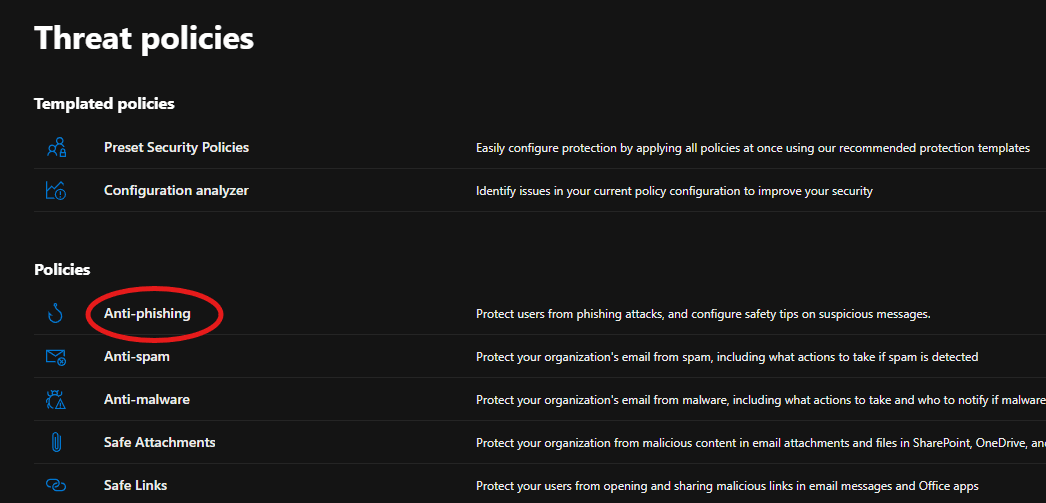
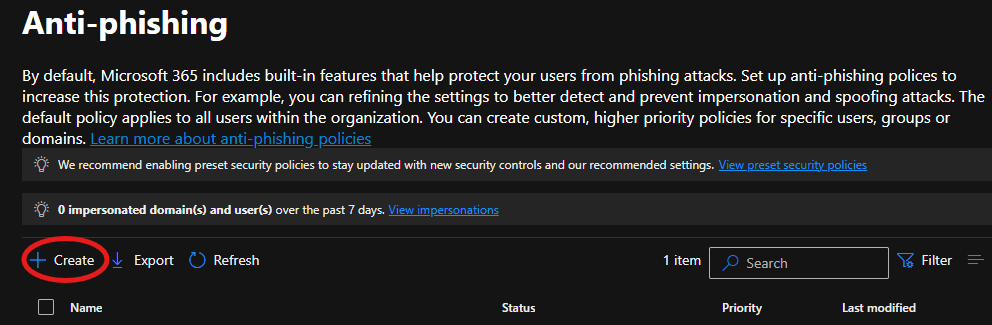
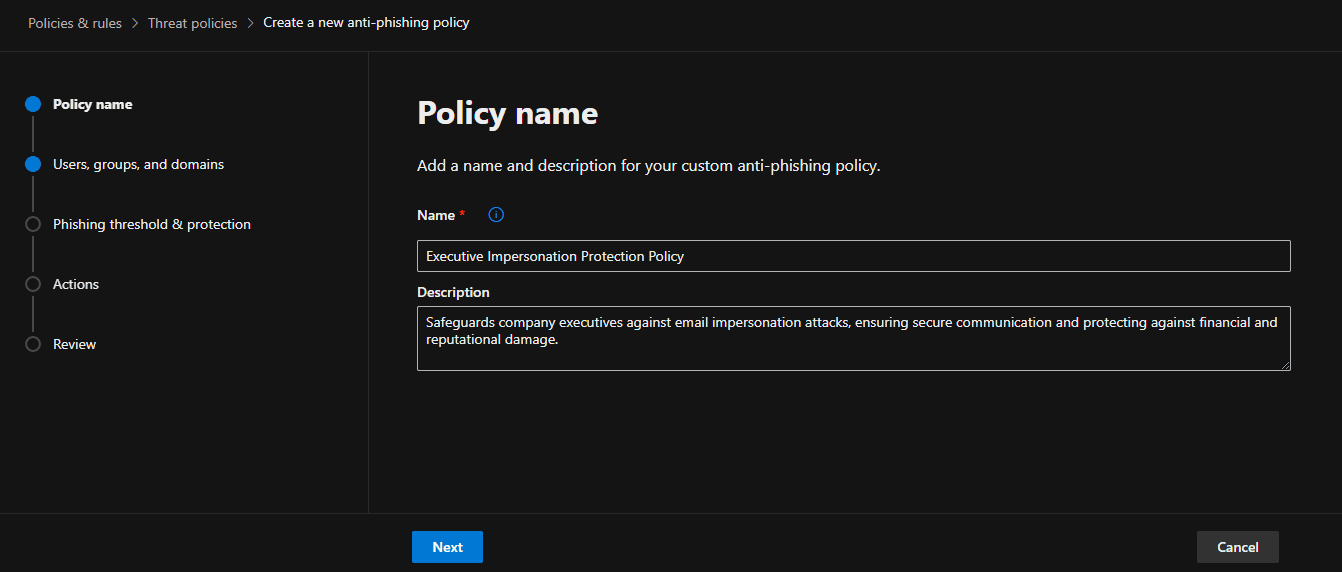
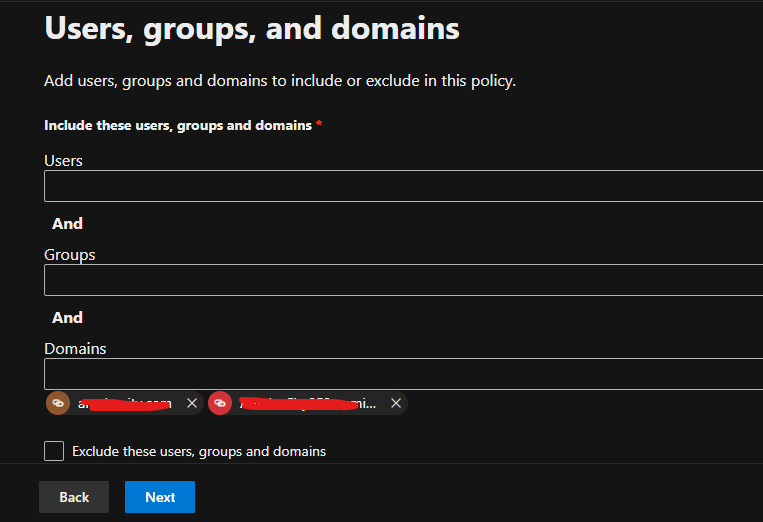
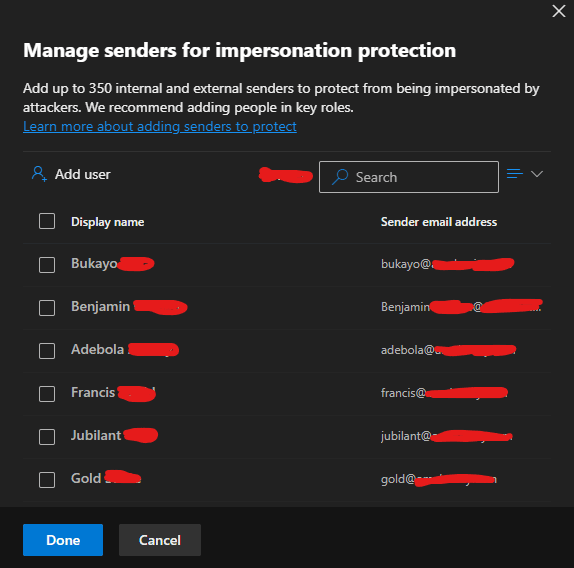
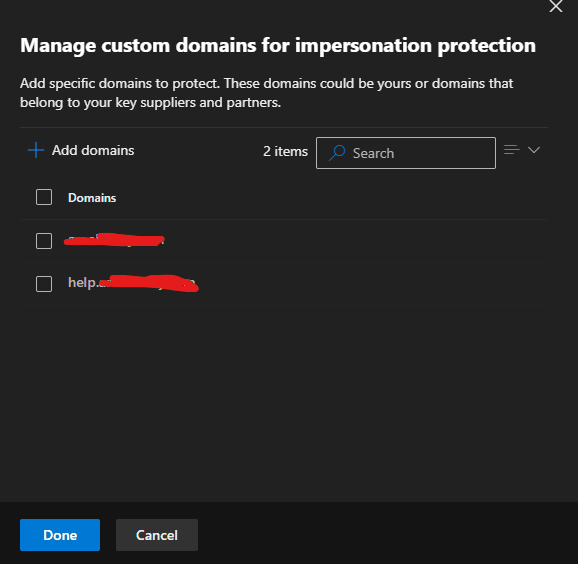
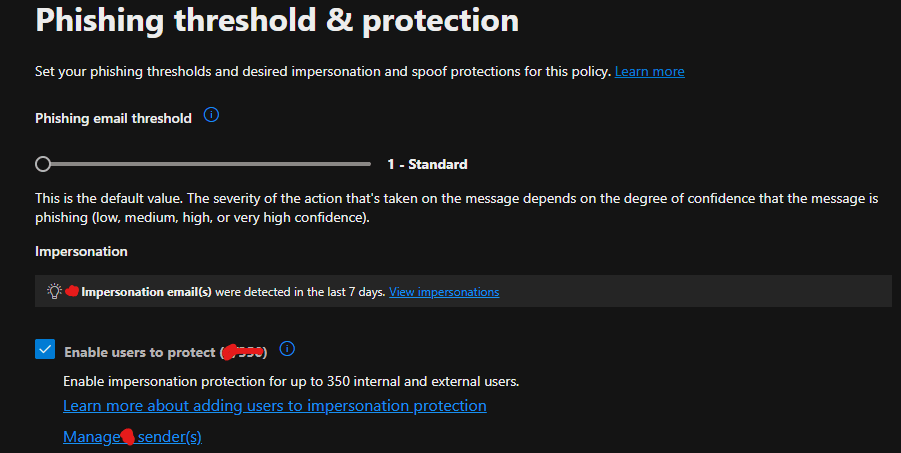
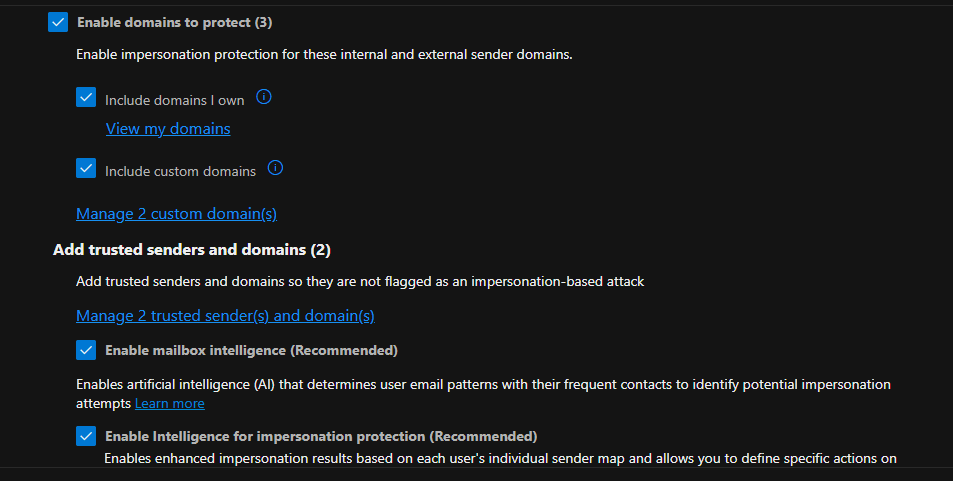
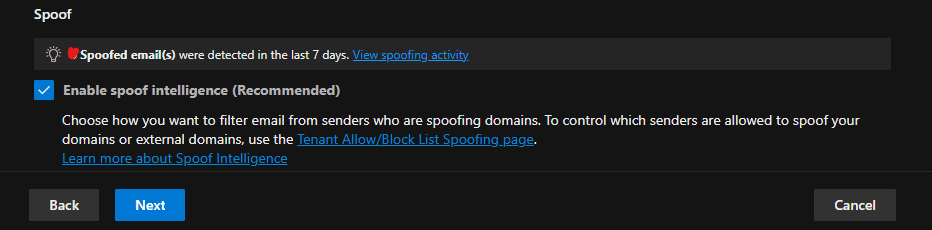
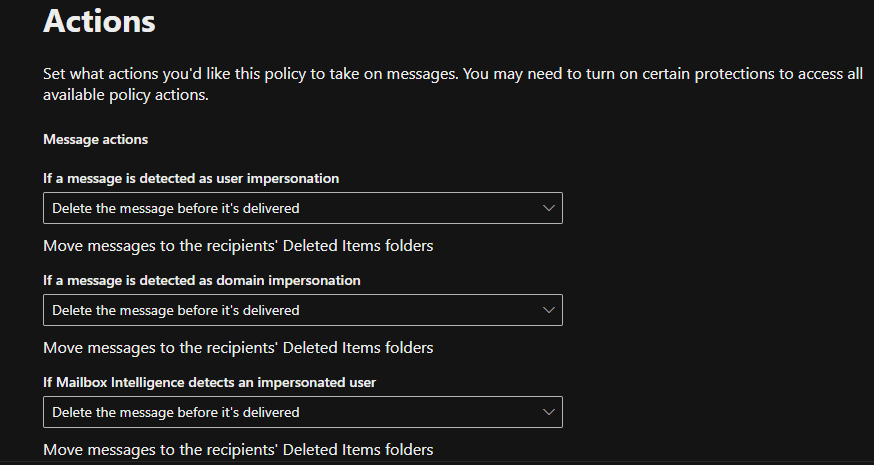
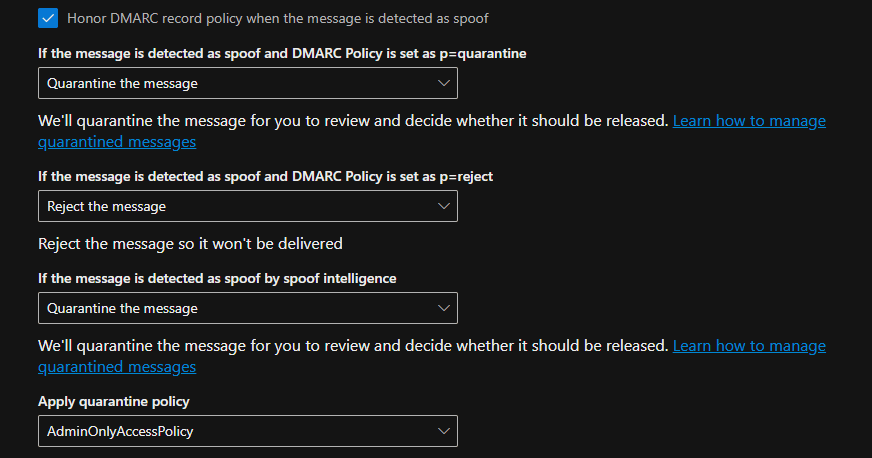
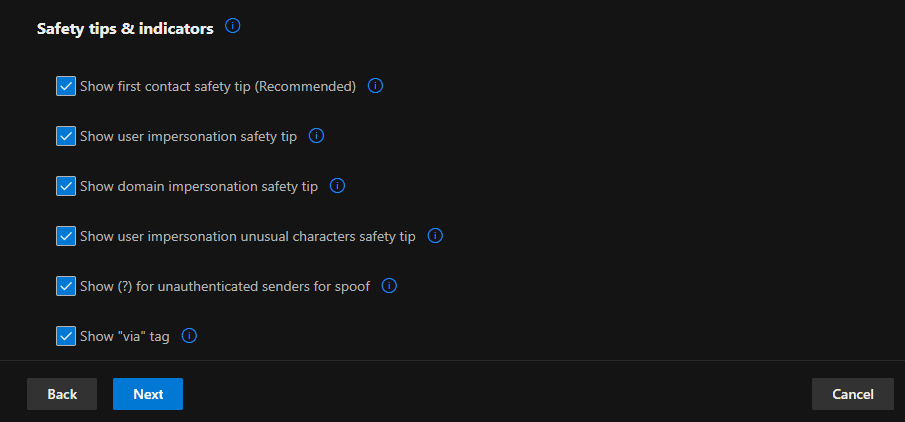
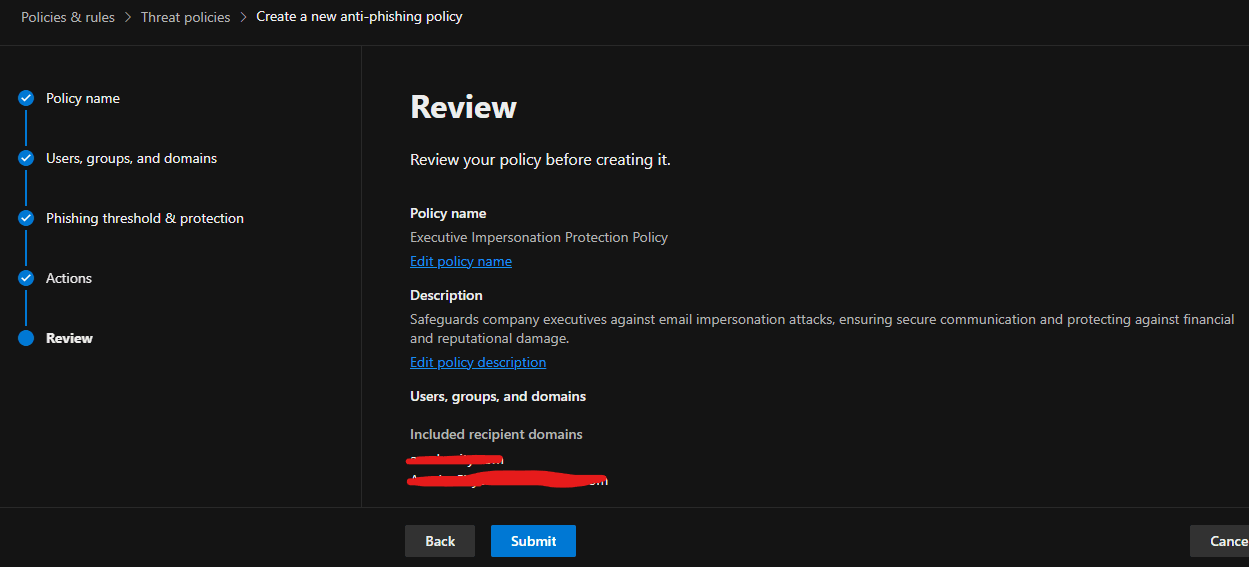
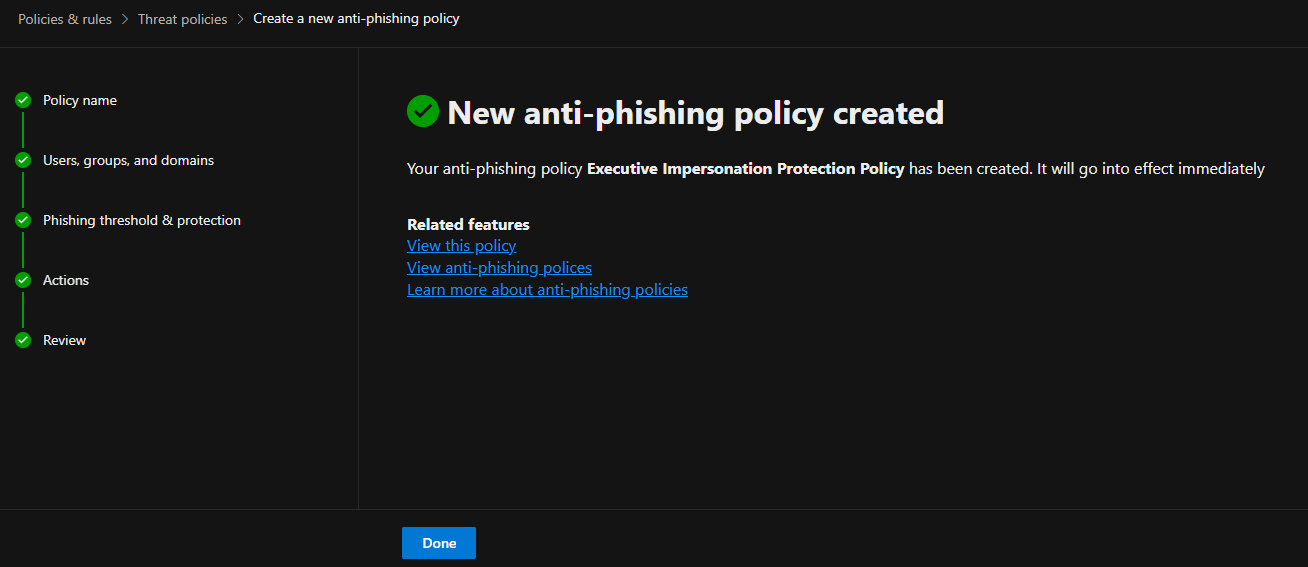
The screenshots above demonstrate how the anti-phishing policy is configured to block emails that mimic and impersonate the company, its staff, and its domain name, thereby protecting all users in the tenant from potential attacks.
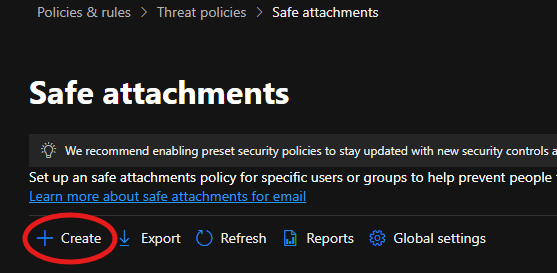
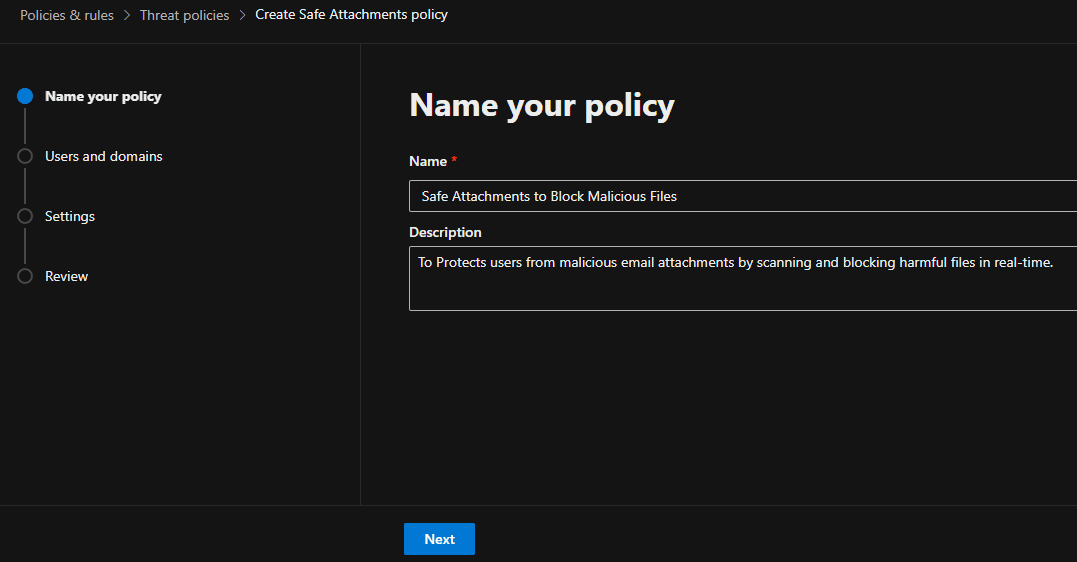
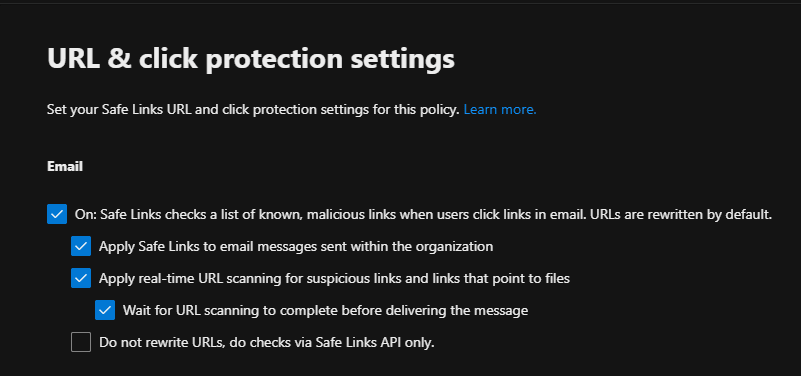
Step 2: Set Up Safe Attachments and Safe Links
Given that many phishing attempts at the company involve malicious attachments and URLs, setting up Safe Attachments and Safe Links is critical to securing email content.
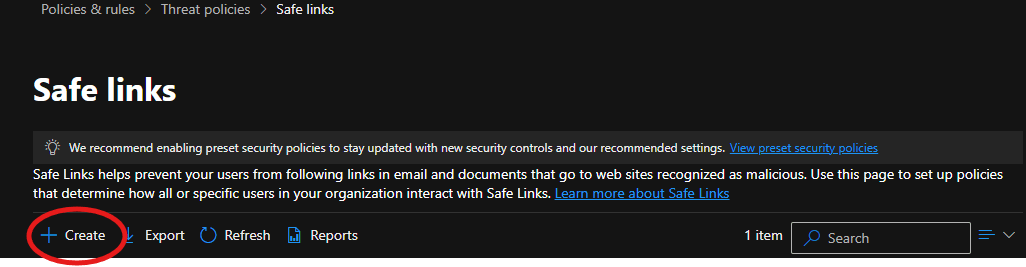
Inside the Microsoft Defender portal, we navigated to Safe Attachments under Threat Policies.
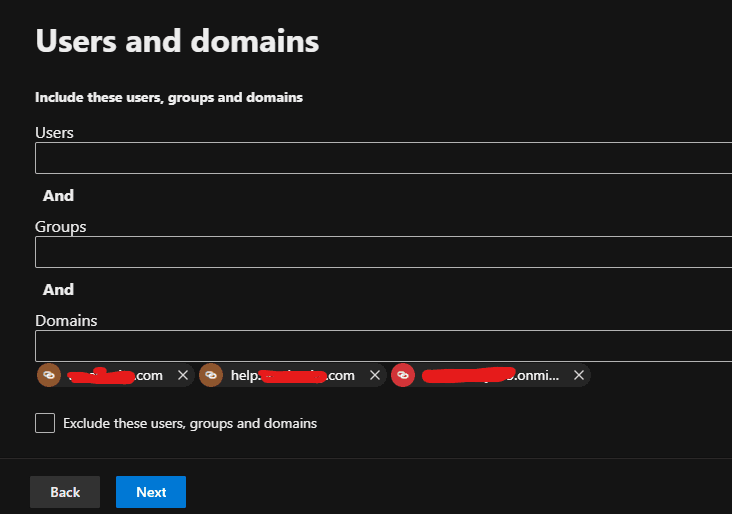
Selecting the domain name for the Safe Attachments policy in Microsoft Defender, as shown in the screenshot above, means that the protection is applied to all email addresses within that domain.
Any email address using that domain will benefit from the Safe Attachments policy which provides an additional layer of security by scanning email attachments in a virtual environment to detect and block malicious content.
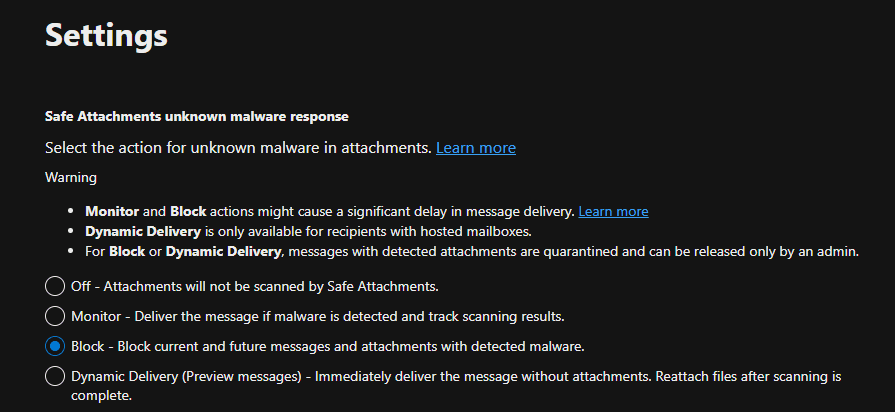
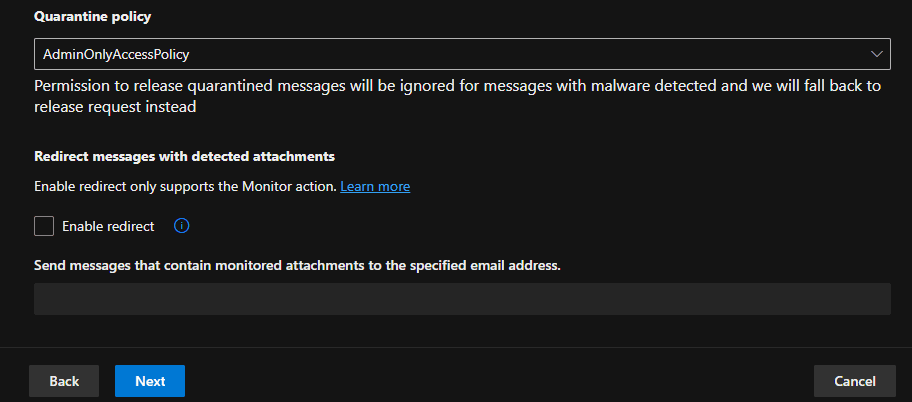
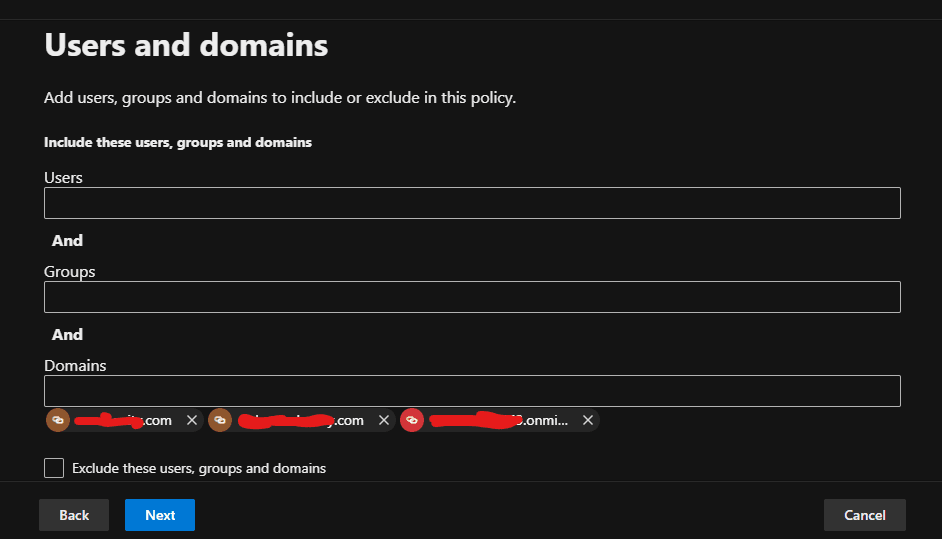
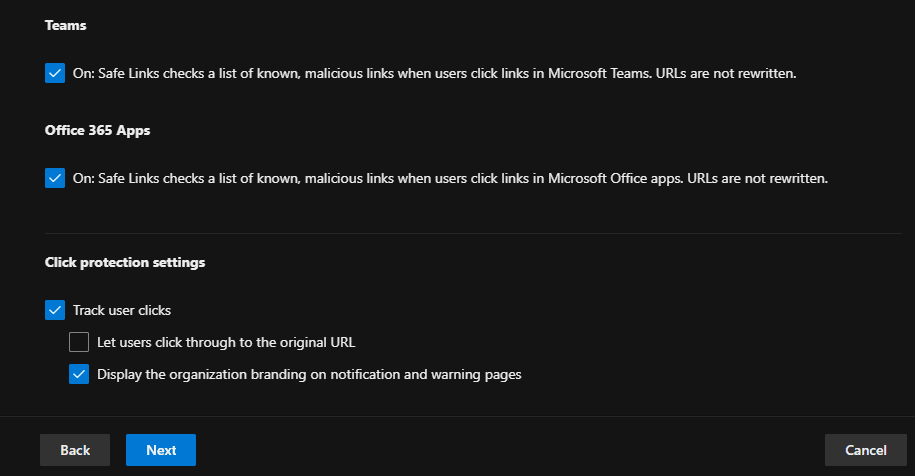
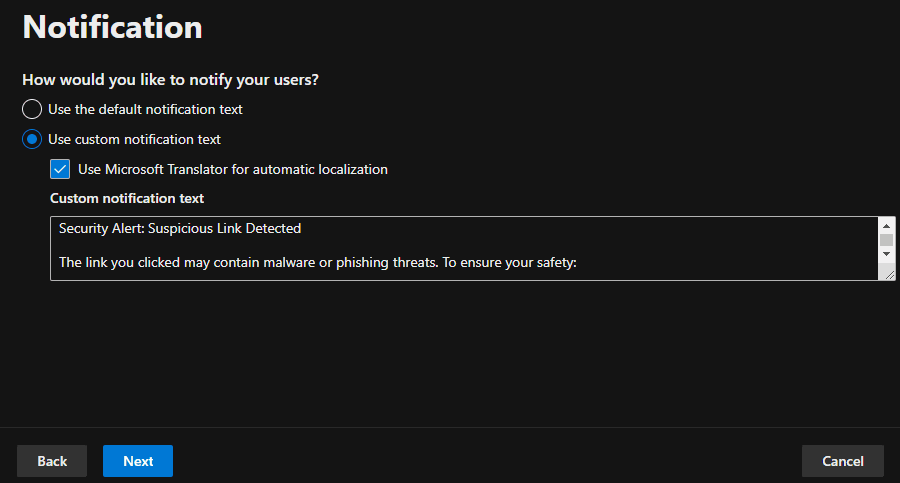
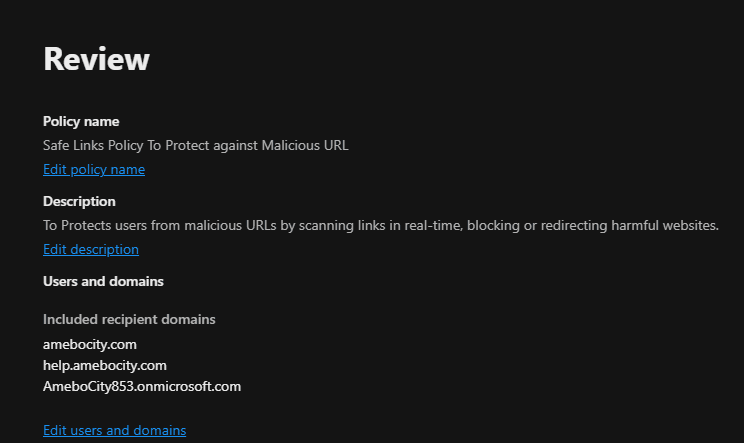
In Safe Links, the policy was configured to scan links within emails in real-time, provide protection against malicious URLs, and redirect or block users who click on dangerous links. The following screenshots show the configuration steps.
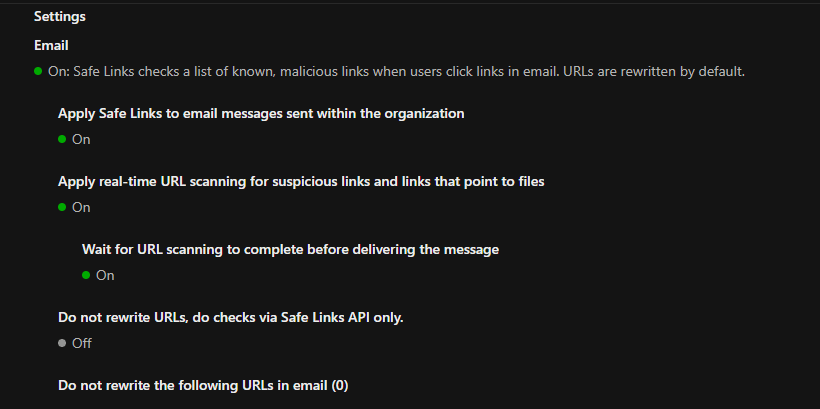
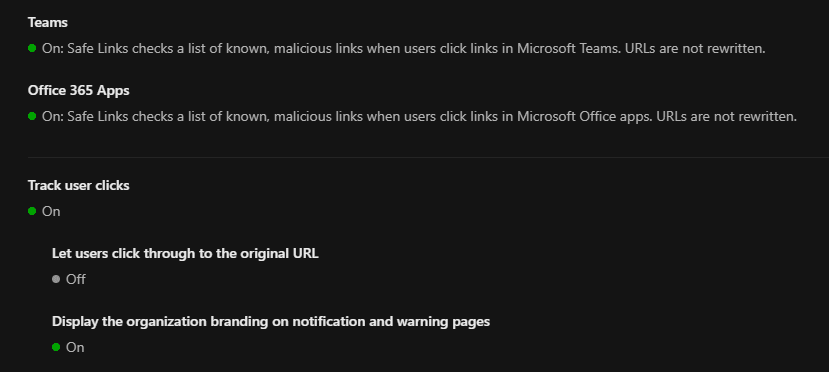
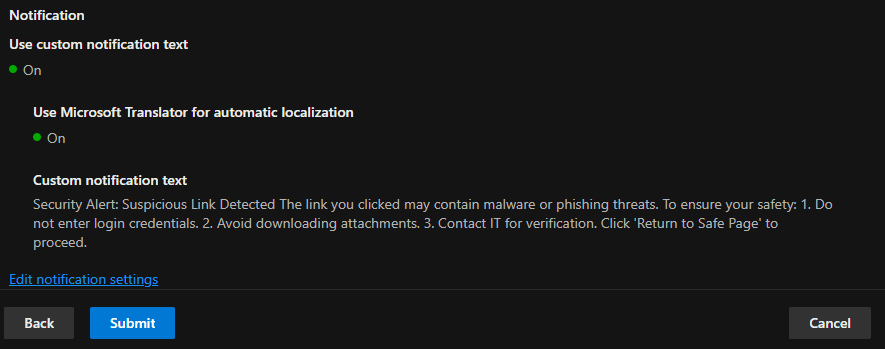
Phishing Simulations to Raise Awareness
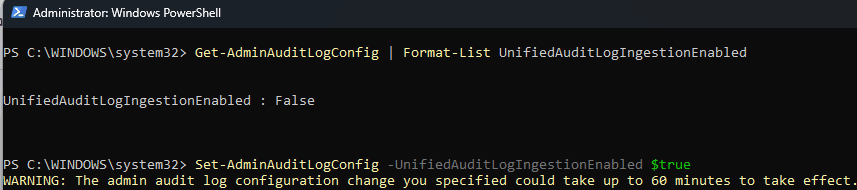
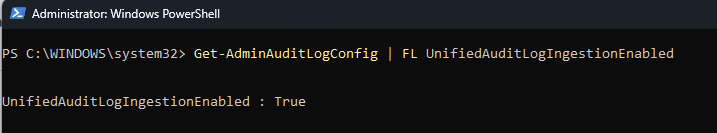
Phishing simulations were conducted to assess employee vulnerability and provide training to prevent actual attacks. However, to utilize reporting capabilities in Attack Simulation Training, auditing must be enabled.
To verify the status, a PowerShell command was run to check if auditing was enabled, which initially returned 'False'. Another command was executed to enable auditing. After waiting a few minutes, a final command was run to confirm the status, and the configuration change successfully showed as 'True,' indicating that auditing was enabled. The following two screenshots show how it was done.
Setting Up the Phishing Simulation
Running phishing simulations in Microsoft 365 using Attack Simulation Training helps you evaluate how aware and resilient your employees are against phishing attacks. Here’s a simple guide to set up and run these simulations effectively.
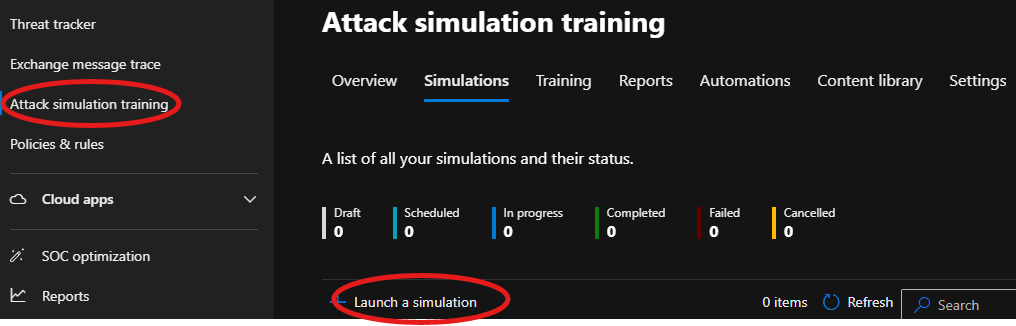
1. Access Attack Simulation Training
To start, go to the Microsoft 365 Defender portal. In the left navigation pane, select Attack Simulation Training under Email & Collaboration.
Note: If you're doing this for the first time, ensure you have the necessary permissions (Global Administrator or Security Administrator roles).
2. Plan the Simulation Campaign
The objective of this simulation is to evaluate employee awareness and understanding of safe email practices across the entire organization. Pre-configured simulation templates will be utilized to facilitate this assessment.
3. Configure the Phishing Simulation
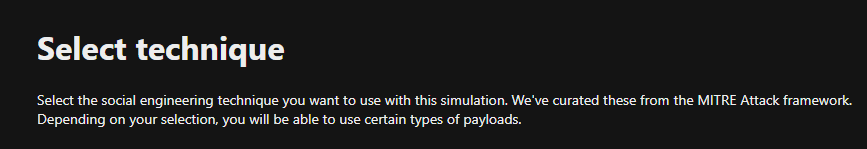
To create a new simulation on the Attack Simulation Training page:
1. Click on Simulations, then select Launch a Simulation.
2. Select a simulation technique.
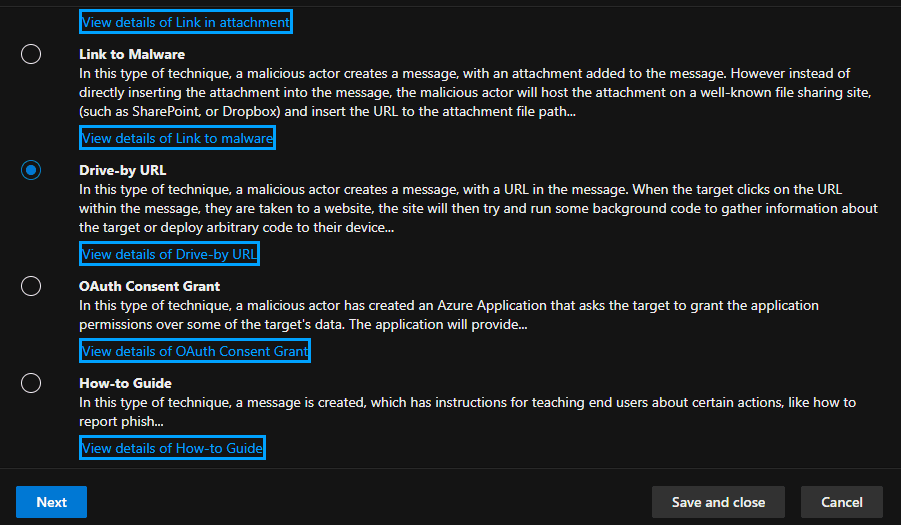
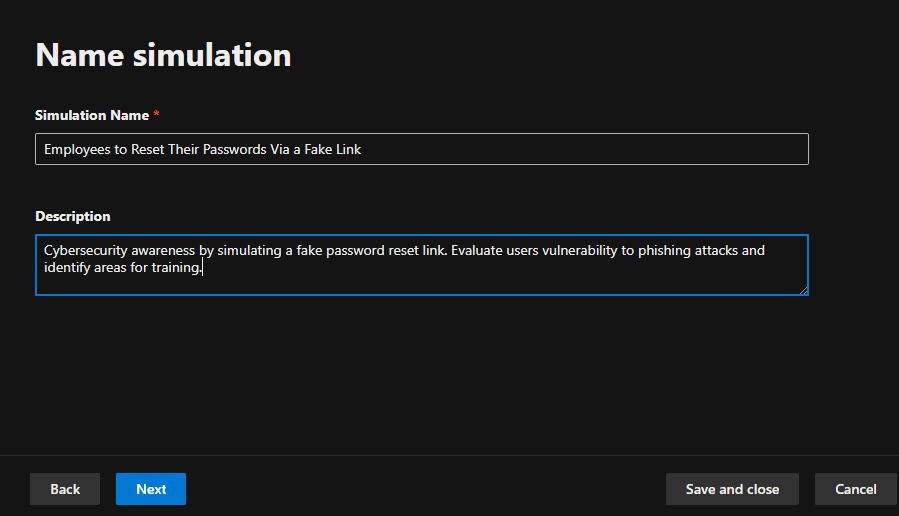
3. Set simulation details by choosing a name and description for the campaign.
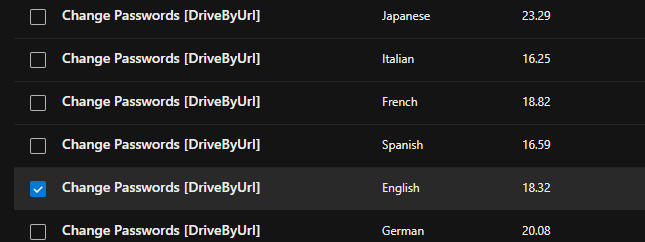
4. Define a realistic scenario where every user in the organization receives an email with a link to change their password by selecting 'Change Password [DriveByUrl].
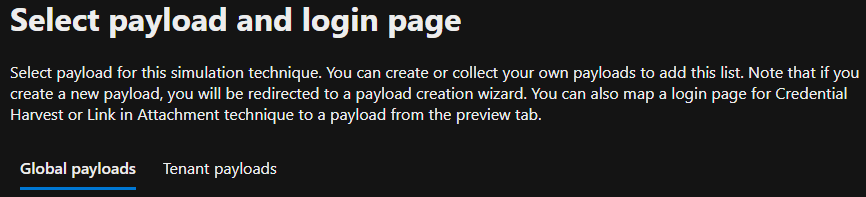
5. To select the payload and login page, pick from available templates provided in the portal by Microsoft.
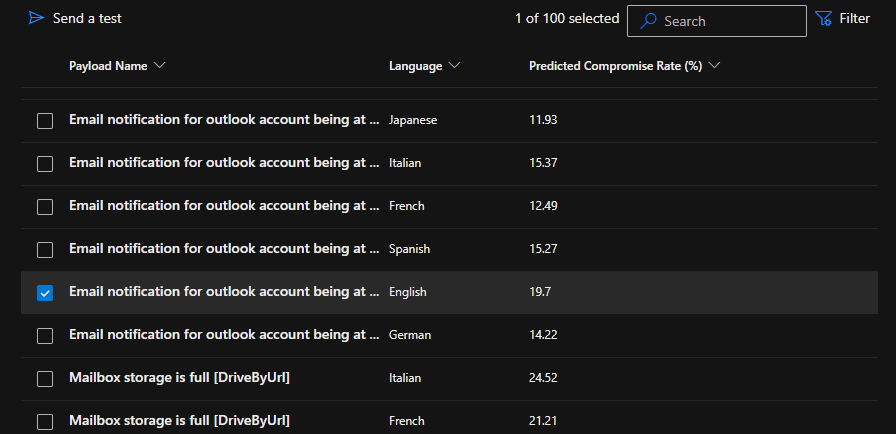
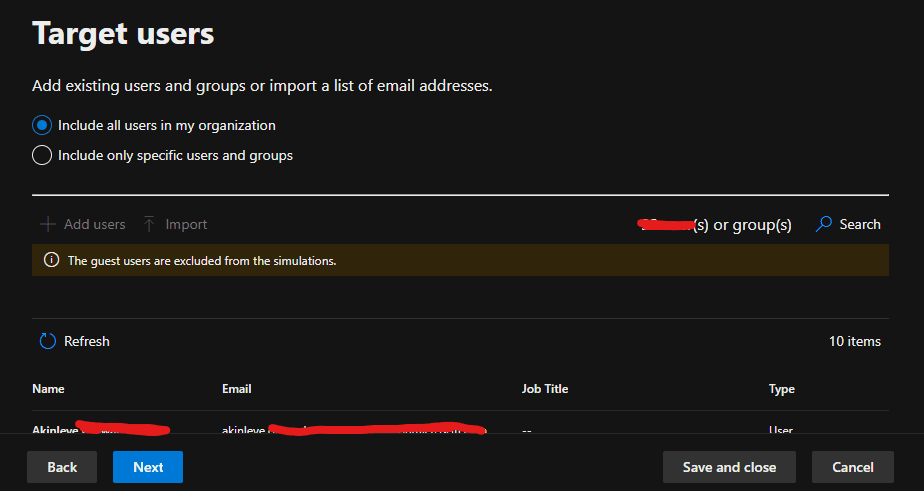
6. Under Target Users, all users in the organization were included, and no users were excluded from the simulation.
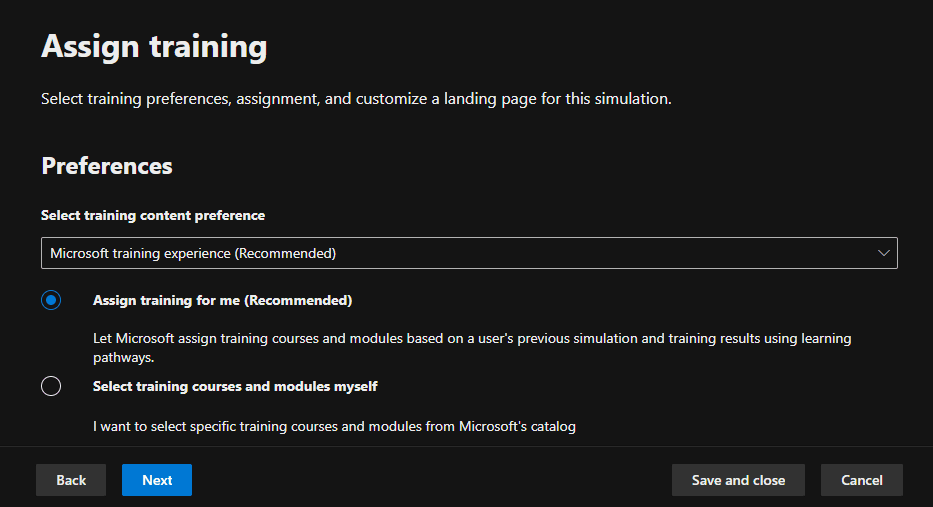
7. Under Assign Training, Microsoft-recommended training courses were chosen, and a training due date was selected.

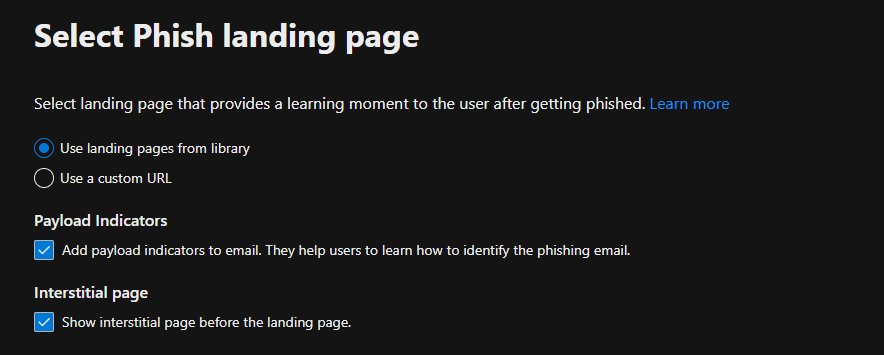
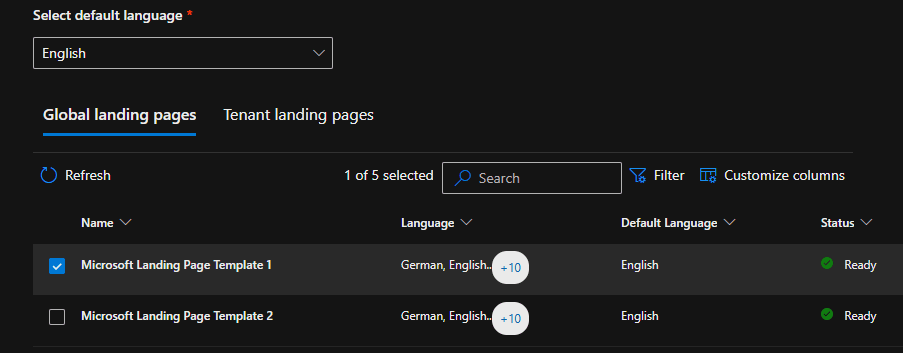
8. Under the Phish Landing Page, we selected a landing page from the Global Landing Page library that provides a learning moment to users after they get phished.
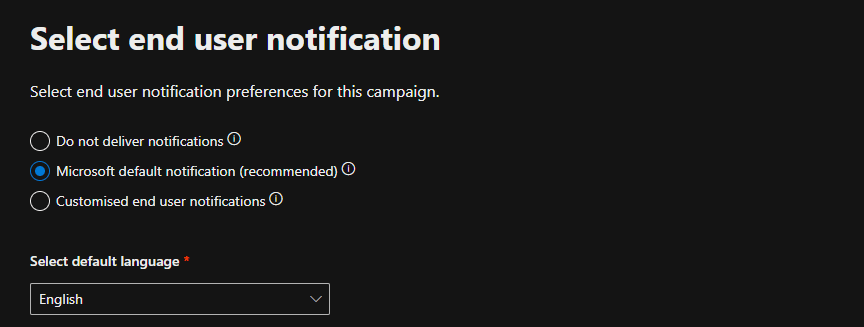
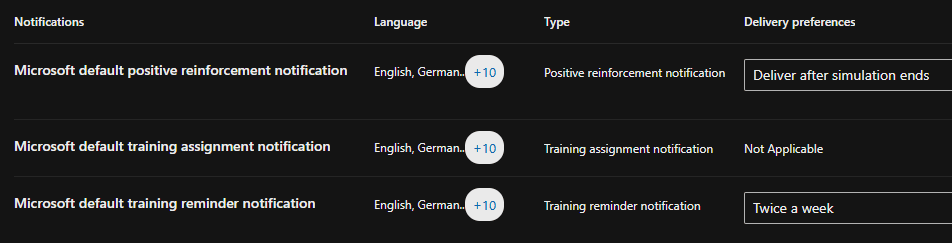
9. Under Select End-User Notification, we selected Microsoft-curated end-user notifications.
4. Schedule the Campaign
Under Launch Details, the desired launch time for the simulation was configured, choosing to launch it as soon as we were done with the configuration. Then, we set the simulation duration to 5 days.
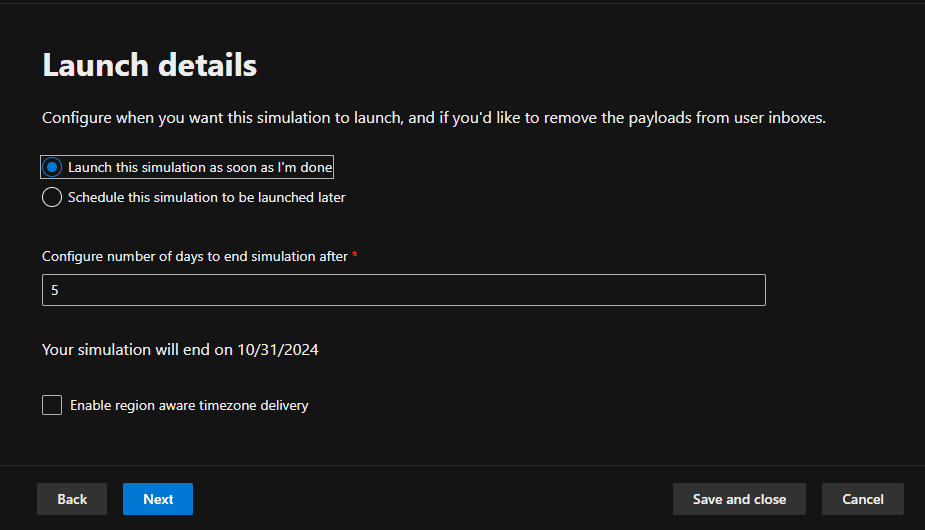
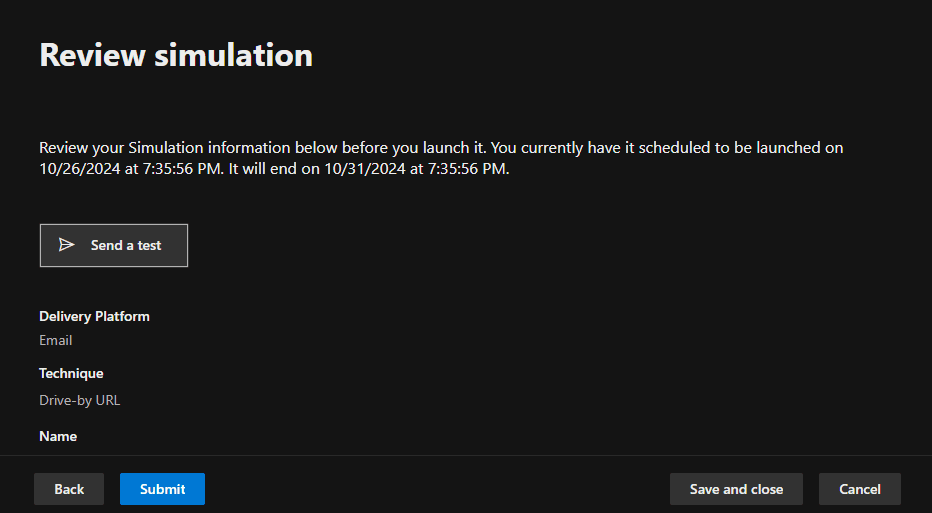
We reviewed the simulation configurations, ensuring all settings were correct. Then, the Submit button was clicked, and the simulation was scheduled for launch.
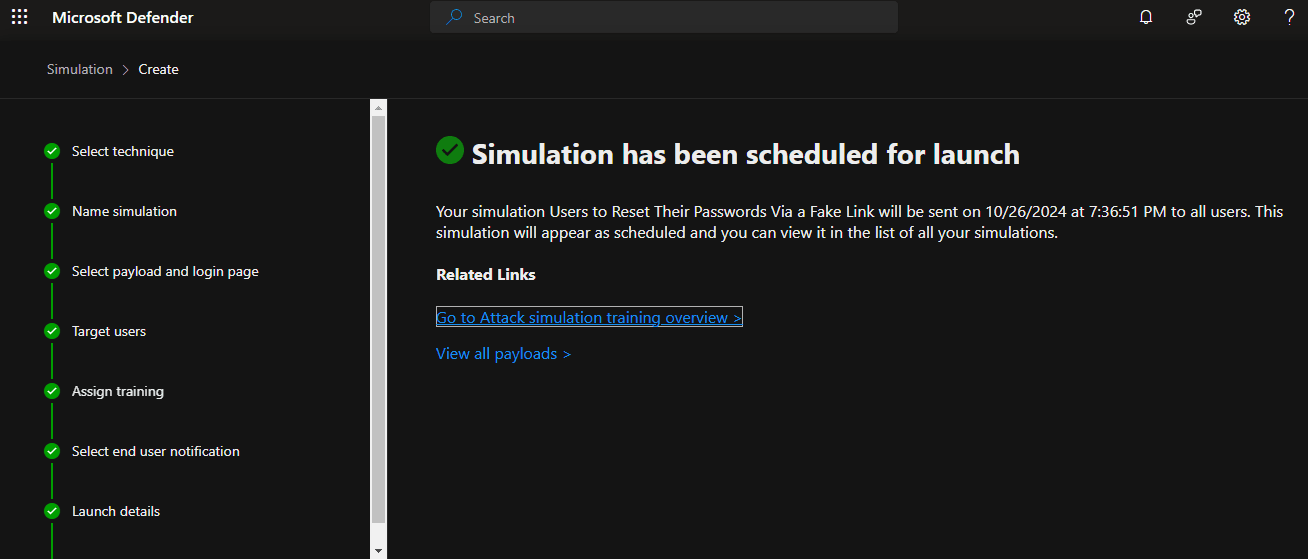
5. Setting Up a Reporting Mechanism for Suspicious Emails
To enable employees to report phishing attacks, we set up a reporting mechanism directly in Outlook. Here are the steps taken:
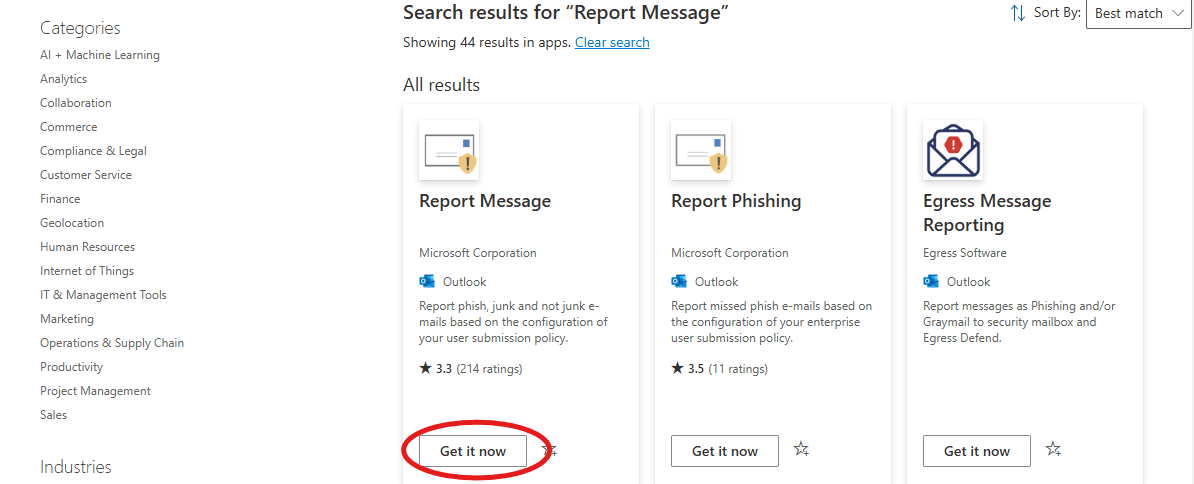
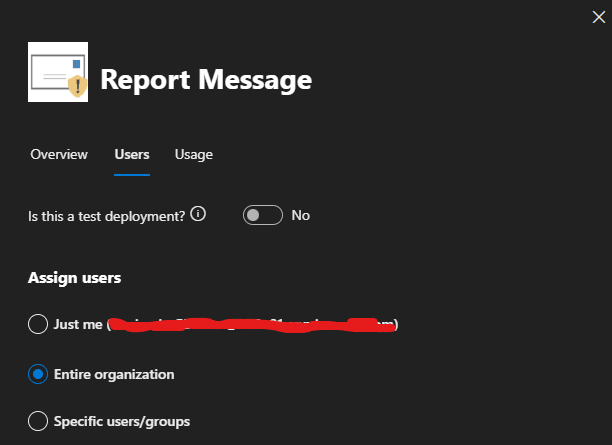
Step 1: Deploy the Report Message Add-in
In the Microsoft 365 admin center, go to Settings > Integrated Apps. Then, search for the Report Message add-in and deploy it to all employees. This allows them to report phishing or suspicious emails directly from their inbox, as shown in the following screenshot.
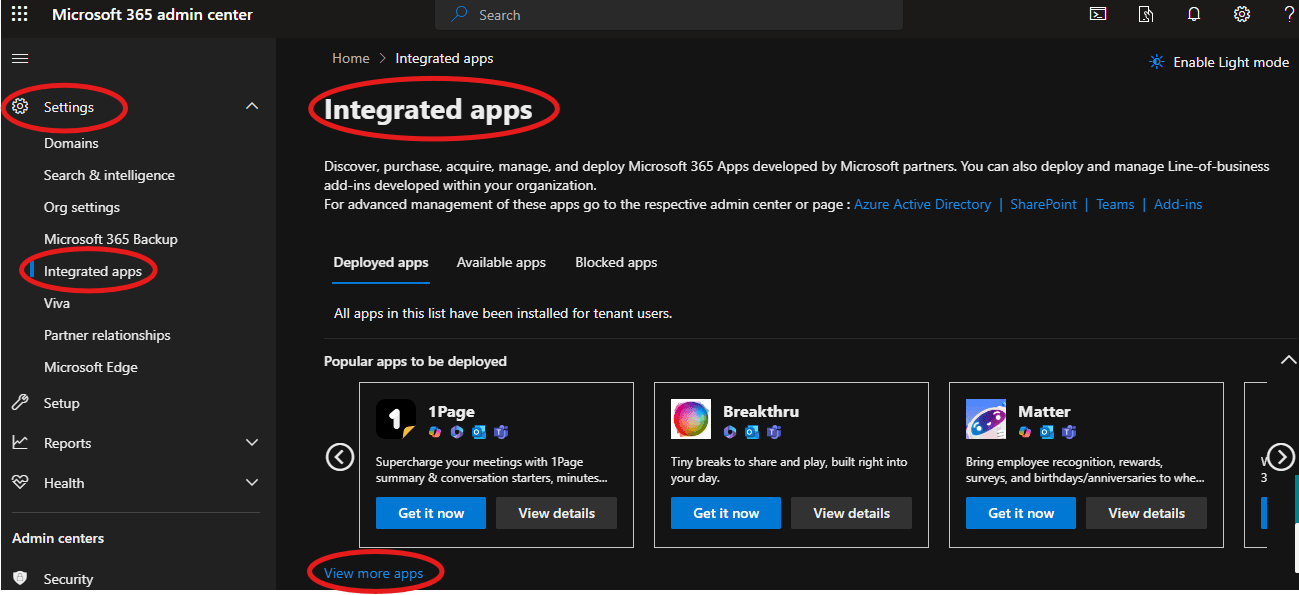
Step 2: Educate Employees on Reporting
The Medha Cloud Security and Compliance team developed email tutorials and guides, including screenshots, that explain how to use the Report Message add-in in Outlook. Additionally, we launched a company-wide email campaign instructing employees to report suspicious emails rather than delete them.
The screenshot below illustrates how a user reported a suspicious email using the Report Message add-in.
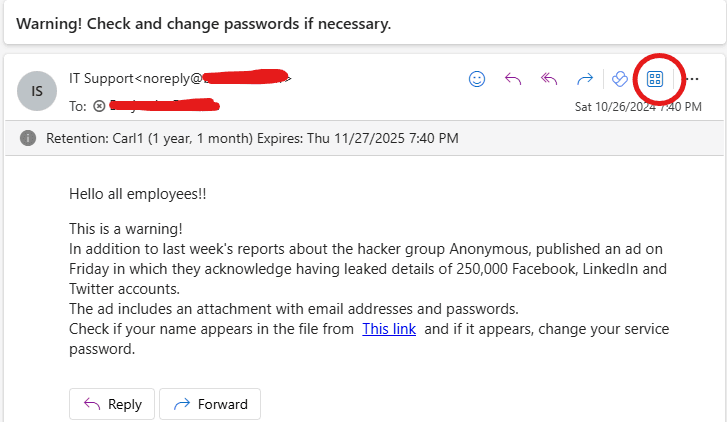
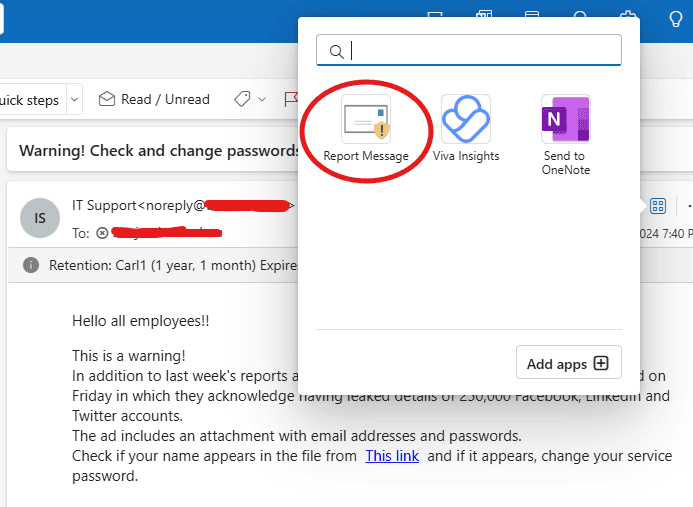
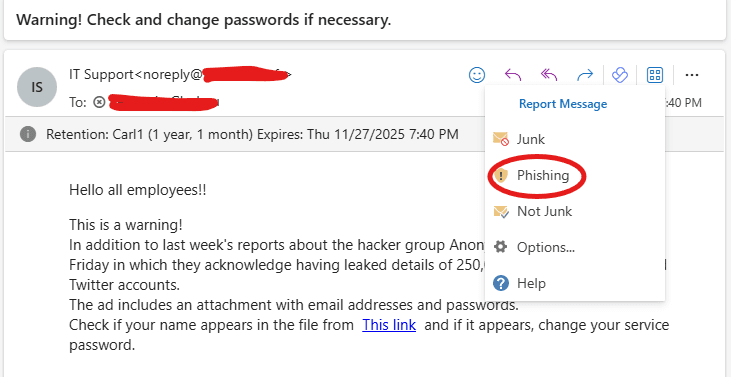
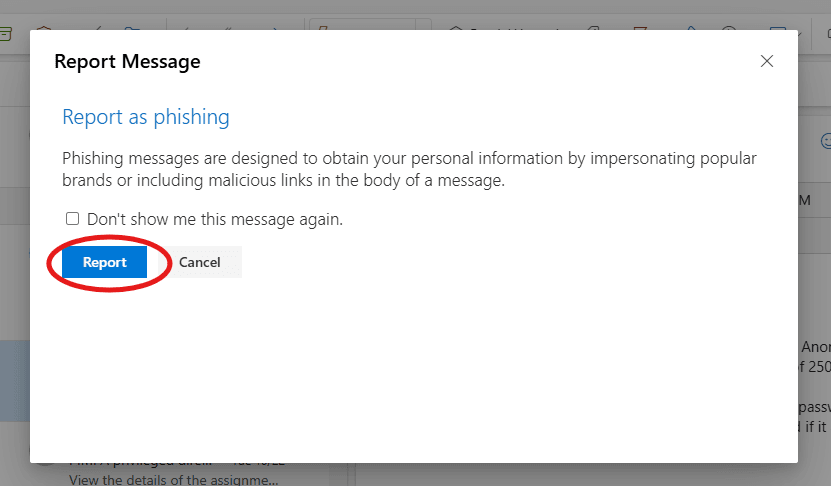
After the user made the report, an email was sent to him by the Security and Compliance team congratulating him for spotting and reporting a phishing email as seen in the screenshot below.
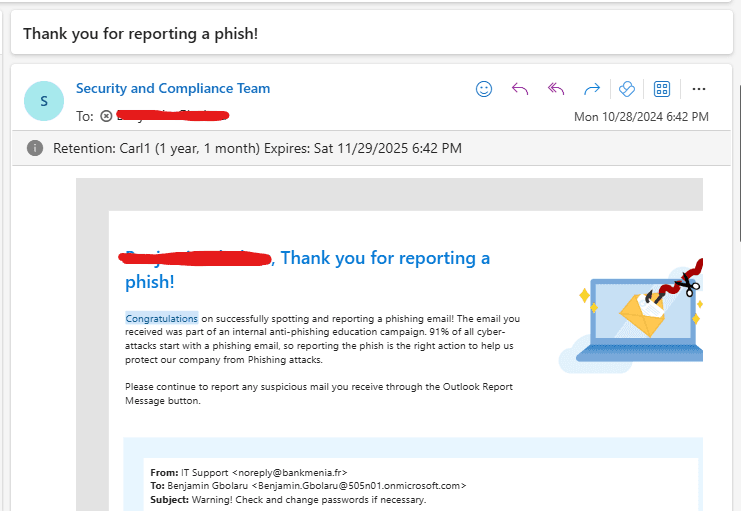
5. Monitor the Campaign Progress
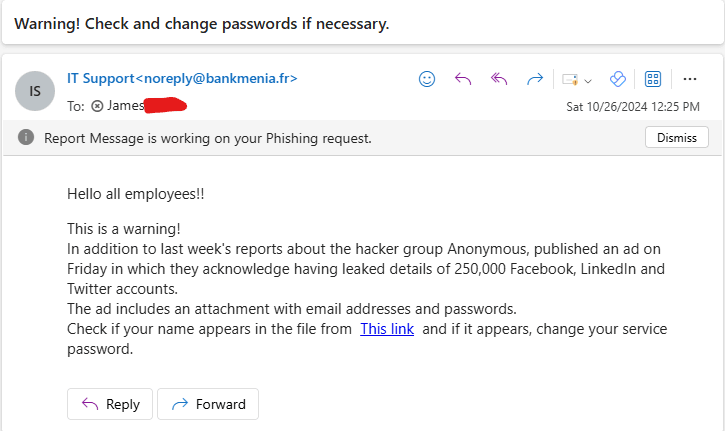
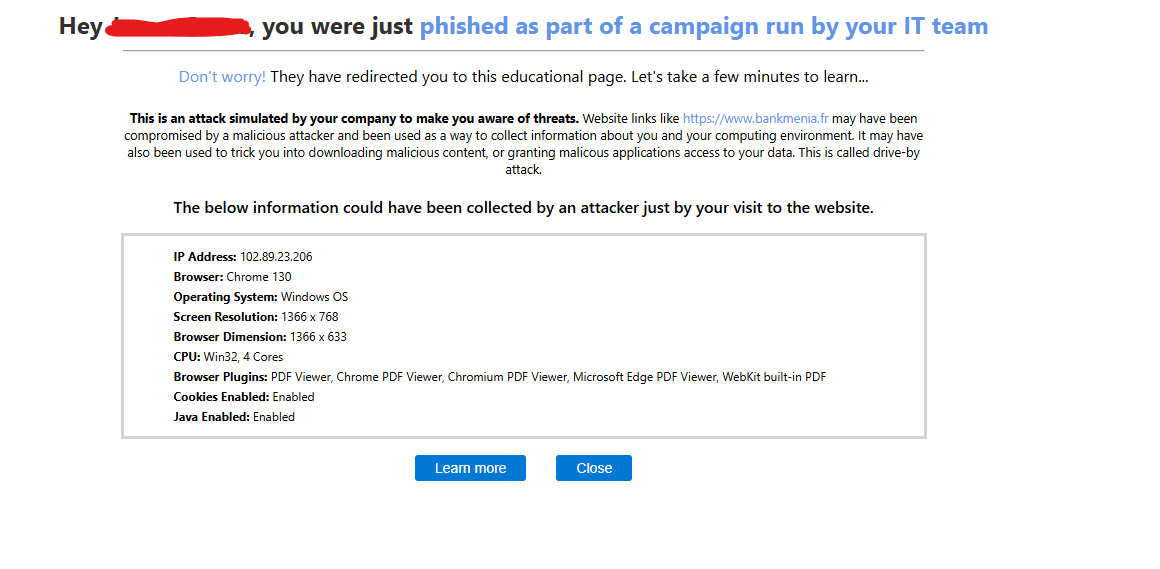
During the campaign, we tracked how many employees clicked the link, submitted credentials, or reported the email using campaign metrics in the Microsoft 365 Defender portal. We redirected those who clicked the link to training resources on phishing awareness.
The screenshot below illustrates a user who clicked the link in the suspicious email and was subsequently directed to phishing awareness training resources.
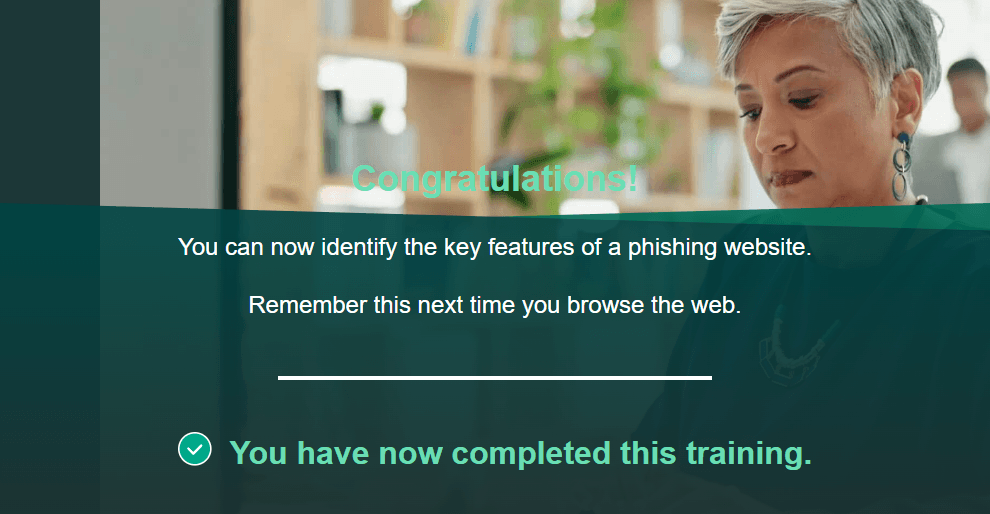
6. Analyze Results and Provide Feedback
After the simulation ends, we reviewed detailed results with the Security and Compliance team to understand:
- Click Rates: The number of employees who engaged with the phishing link.
- 20.00% of users (50/500) clicked the phishing link.
(See screenshot below)
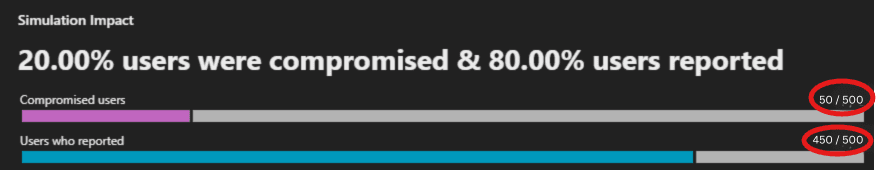
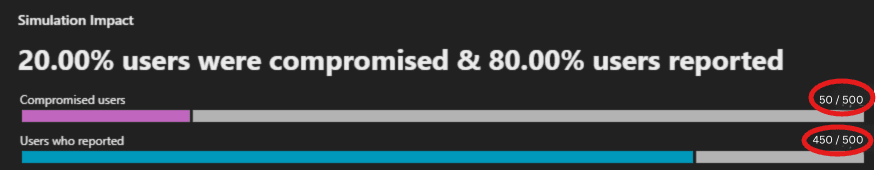
2. Report Rates: The number of employees who reported the simulation as phishing.
- 80.00% of users (450/500) reported the email.
(See screenshot below with 450 items in Red Circle)
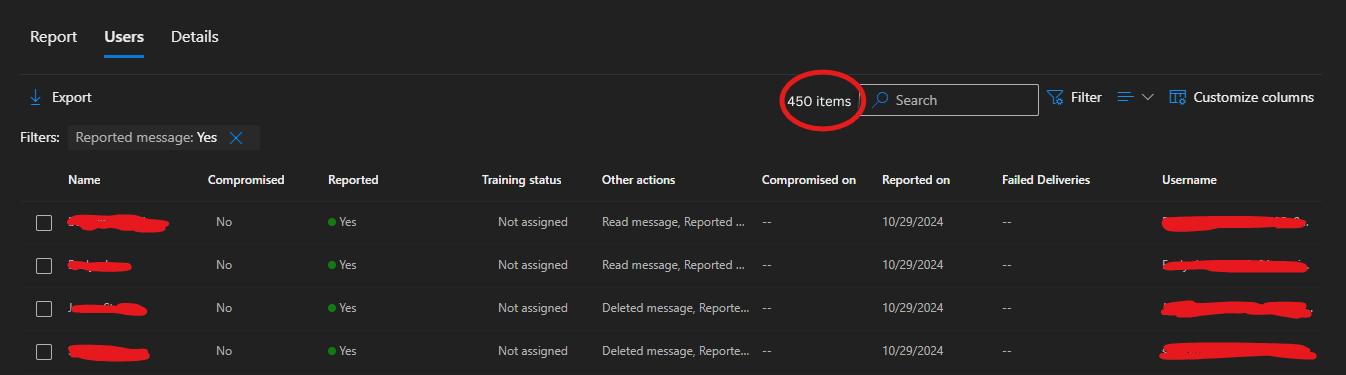
- 450 Users Reported (See screenshot below{450 items in Red Circle})
7. Run Follow-Up Training
For employees who fell for the simulation, the Security and Compliance team assigned targeted training to reinforce awareness, providing modules and guidance from Microsoft to improve cybersecurity behavior.
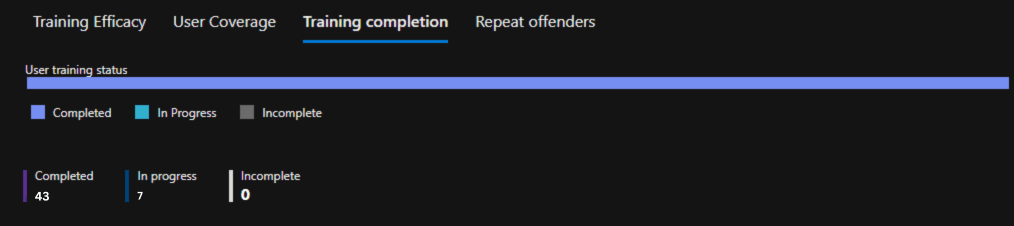
Training Completion:
Employees who engaged with the phishing link.
Training Status:
- Completed: 43 users
- In Progress: 7 users
- Incomplete: 0 users
Final Outcome:
The project objectives were successfully achieved by the Medha Cloud Security and Compliance Team, as evidenced by the following key accomplishments:
- Implementation of Microsoft Defender for Office 365 to safeguard against email-borne threats, including phishing, malware, and malicious links.
- Conducted phishing simulations to evaluate employee awareness and provide targeted training.
- Established a reporting mechanism, enabling employees to report suspicious emails directly from Outlook.
Final Thought
In today’s rapidly evolving threat landscape, your organization’s security is more important than ever. At Medha Cloud, we have a team of certified and qualified professionals ready to assist you in tackling cybersecurity and attack challenges. Whether it's protecting against phishing, malware, ransomware, or other threats, we specialize in configuring and optimizing your cloud security with the latest Microsoft solutions, including Microsoft Defender for Office 365.
Just like we successfully implemented Defender for Office 365 for a mid-sized company with 500 users, our experts will work with you to assess your needs, implement tailored security policies, and provide ongoing support to ensure your organization stays protected from emerging threats. By leveraging advanced features such as anti-phishing policies, Safe Attachments, and Safe Links, we can help reduce the risks from harmful emails and ensure that malicious messages, impersonation attempts, and suspicious attachments are stopped before they reach your employees.
The work we’ve done for other organizations, including phishing simulations and employee training, has been key in raising awareness and fostering a proactive security culture. We will help you implement these strategies, equipping your employees with the knowledge and tools they need to recognize phishing attempts and report suspicious emails.
Don’t wait until it’s too late. Contact Medha Cloud today to secure your cloud environment and fortify your defense against cyberattacks. Let us help you build a proactive, resilient security posture that safeguards your sensitive data and organizational integrity. With our expert assistance, your organization will be better equipped to handle the changing landscape of cyber threats.
Contact Us Today
- Email: sales@medhahosting.com
- Phone: +1 646 775 2855 / +91 93536 44646
Topics

Sreenivasa Reddy G
Founder & CEO • 15+ years
Sreenivasa Reddy is the Founder and CEO of Medha Cloud, recognized as "Startup of the Year 2024" by The CEO Magazine. With over 15 years of experience in cloud infrastructure and IT services, he leads the company's vision to deliver enterprise-grade cloud solutions to businesses worldwide.

