How to Manage Entra ID Emergency Access Accounts: Best Practices by Medha Cloud

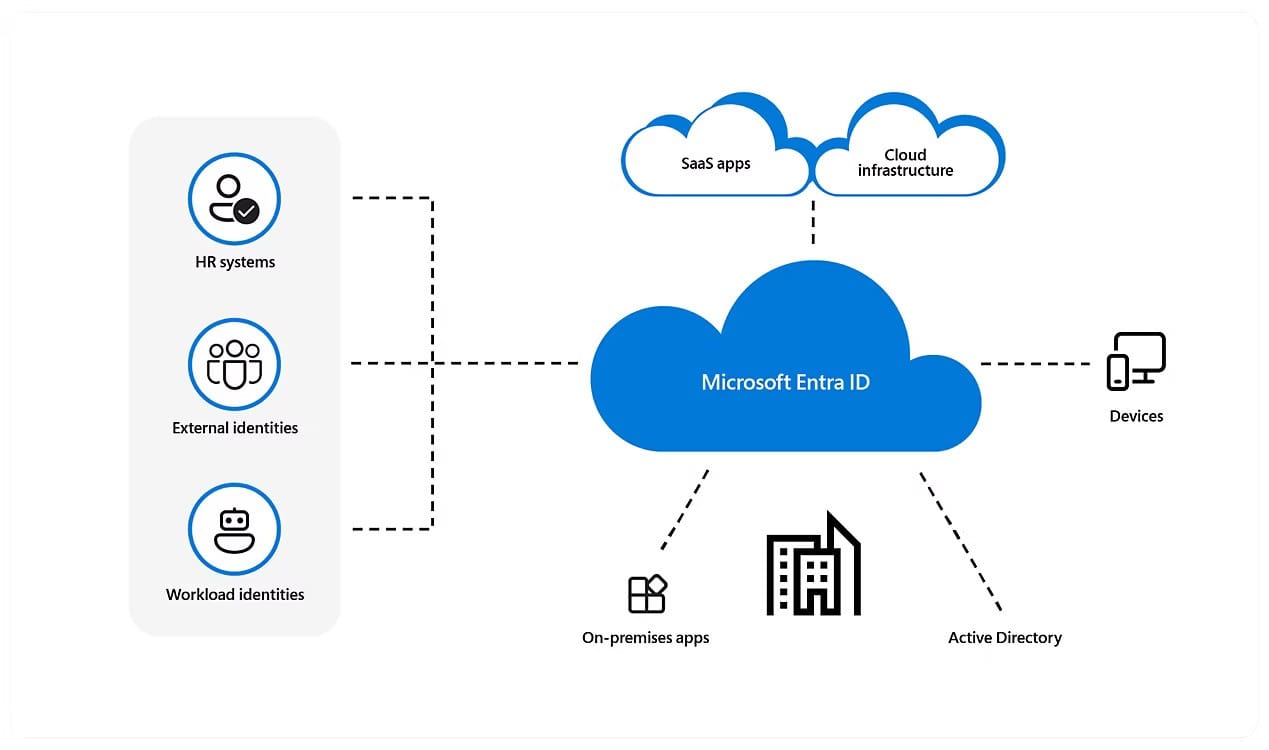
As organizations like yours adopt advanced security measures, managing emergency access accounts (commonly called “break glass” accounts) in Entra ID (formerly Azure AD) becomes a critical aspect of tenant administration. These accounts are your safety net when regular admin accounts lose access, such as during an MFA outage or accidental misconfiguration.
At Medha Cloud, we’ve seen firsthand how essential it is to implement a robust yet practical approach to managing emergency access accounts. In this article, we’ll break down the best practices in simple terms, ensuring your accounts are secure, accessible, and compliant.
What Are Emergency Access Accounts?
Emergency access accounts are administrator accounts specifically designed to bypass security policies in extreme cases. Think of them as your backup keys to the kingdom, only to be used when all other access methods fail.
These accounts should:
- Be excluded from conditional access policies and Privileged Identity Management (PIM).
- Have highly secure credentials, including long passwords and hardware-based MFA.
- Be available to designated personnel during emergencies.
Best Practices for Managing Entra ID Emergency Access Accounts
1. Keep It Simple: Two Accounts per Tenant
- Why two? Redundancy. If one account fails or gets compromised, you have another to fall back on.
- Assign one account to your organization (Medha Cloud, in this case) and the other to your customer or a trusted administrator.
2. Secure Your Passwords
- Use long, complex passwords with random characters (16-24 characters is ideal).
- Store these passwords securely in a tamper-proof hardware safe or a password management solution like:
- Azure Key Vault
- LastPass Enterprise
- 1Password Business
Pro Tip: Avoid using shared documents or spreadsheets for storing passwords.
3. Implement MFA with Hardware Security Keys
MFA (Multi-Factor Authentication) adds an extra layer of protection, and hardware security keys like Yubikeys are perfect for emergency accounts. Here’s how to manage them:
- Assign 2-3 Yubikeys per account.
- Store them in separate, secure locations (e.g., company headquarters, a disaster recovery site, and a secondary office).
Why Yubikeys?
They’re physical devices that can’t be hacked remotely, making them the gold standard for MFA.
4. Use a Secure Digital Vault
While hardware safes are great, a digital password vault provides faster access and better traceability. Solutions like Azure Key Vault allow you to:
- Store credentials securely.
- Restrict access to only authorized personnel.
- Monitor access logs for accountability.
5. Test and Rotate Regularly
Break glass accounts are only helpful if they work when you need them. Here’s how to keep them functional:
- Test quarterly: Ensure accounts and MFA methods are accessible.
- Rotate passwords annually or after personnel changes.
- Keep detailed logs of testing activities.
6. Document and Train Your Team
Prepare clear documentation on how to use the emergency access accounts.
- Store this documentation in an immutable format (e.g., Azure Blob Storage with write-once-read-many policies).
- Train your team to ensure they understand when and how to use the accounts responsibly.
Enhancing Your Setup with Medha Cloud
At Medha Cloud, we specialize in creating secure, scalable solutions for managing Microsoft 365 and Entra ID environments. Here’s how we can help:
Advanced Solutions for Emergency Access
- Dedicated Mobile Devices for MFA:
We can assign secure, dedicated devices pre-configured with authenticator apps for emergency access accounts. - JIT Integration Without Risk:
Just-in-Time (JIT) role assignment is great for security, but it shouldn’t involve emergency accounts. We help ensure your JIT policies don’t interfere with break glass access. - Custom Logging and Alerting:
Medha Cloud sets up automated alerts for unusual activity on emergency accounts, ensuring quick detection and response. - Password Vault Integration:
Using tools like Azure Key Vault, we ensure credentials are secure and accessible only when needed.
Common Mistakes to Avoid
- Integrating emergency accounts with PIM or Conditional Access Policies: These accounts must bypass standard security policies to remain accessible during crises.
- Neglecting periodic testing: Unused accounts can fail due to misconfiguration or forgotten credentials.
- Relying on a single access method: Always have multiple access options, including geographically distributed Yubikeys or vaults.
Conclusion
Managing Entra ID emergency access accounts is essential for ensuring business continuity and security. By following these best practices—using secure storage, hardware MFA, periodic testing, and proper documentation—you can protect your tenant from lockouts while maintaining compliance.
At Medha Cloud, we empower businesses to implement these strategies seamlessly. If you’re looking for expert guidance or advanced solutions for Entra ID and Microsoft 365, get in touch with us today!
Let’s ensure your emergency access is never out of reach.
Reach us at:
- India: +91 93536 44646
- US: +1 646 775 2855
- Website: medhacloud.com
- Email: info@medhacloud.com

Sreenivasa Reddy G
Founder & CEO • 15+ years
Sreenivasa Reddy is the Founder and CEO of Medha Cloud, recognized as "Startup of the Year 2024" by The CEO Magazine. With over 15 years of experience in cloud infrastructure and IT services, he leads the company's vision to deliver enterprise-grade cloud solutions to businesses worldwide.
