
Microsoft Entra ID offers powerful features to enhance organizational security posture, reduce risk, and improve compliance. This report explores three key aspects: Access Reviews, Admin Units, and Privileged Identity Management (PIM). I am pleased to provide a detailed report on how to utilize these powerful features in the Microsoft Entra ID Admin Center. I will explore their benefits, configurations, and best practices to maximize Entra ID’s potential.
Microsoft Entra ID’s access reviews help organizations manage user access to groups, applications, and roles. Regular reviews ensure only the right people have access.
By using access reviews, organizations can efficiently manage user access, reduce risk, and improve compliance.
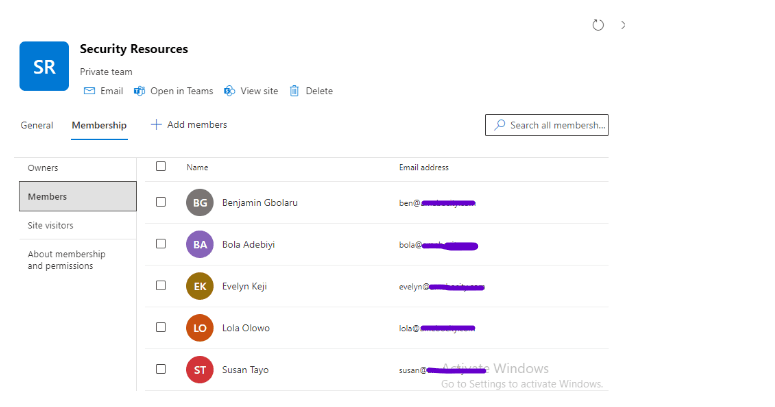
To configure access reviews, you need to create access review policies, specify reviewers, and set frequencies. Using the following scenario, I will demonstrate how to achieve this: An IT Security Manager at a large organization wants to ensure that only active and authorized members of the ‘Security Resources’ group have access to sensitive security resources. To achieve this, the manager decides to conduct a regular Access Review for the ‘Security Resources’ group, which consists of five members: Benjamin, Susan, Evelyn, Bola, and Lola.
This is a screenshot showing the members of the Security Resources Group.
Below is the step-by-step guide I followed with screenshots to configure access reviews using the scenario.
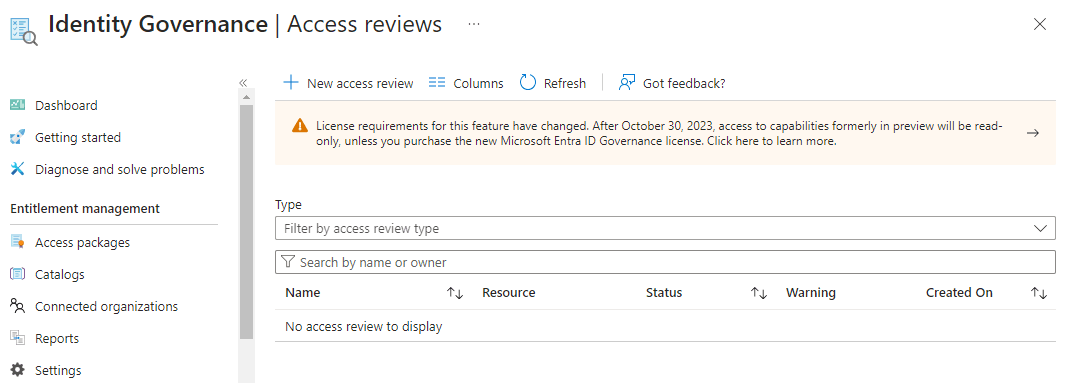
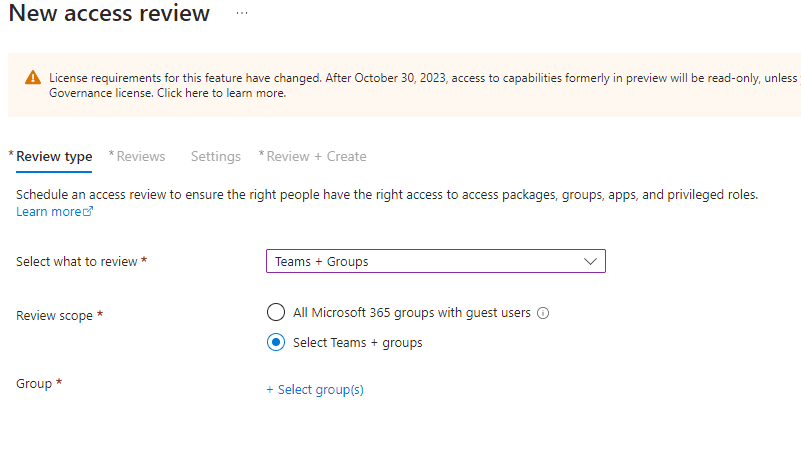
Step 1: Navigating to Access Review I logged in to the Microsoft Entra ID Admin Center, navigated to Identity Governance, and clicked on Access Reviews. Then, I clicked on ‘New access review’.
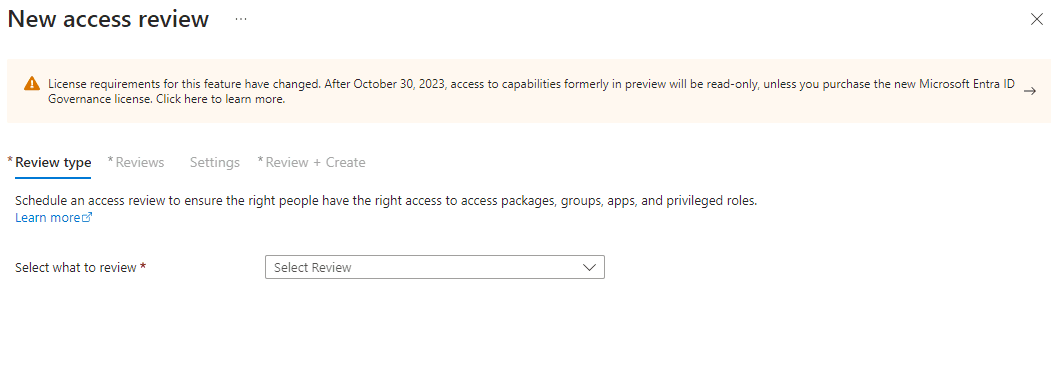
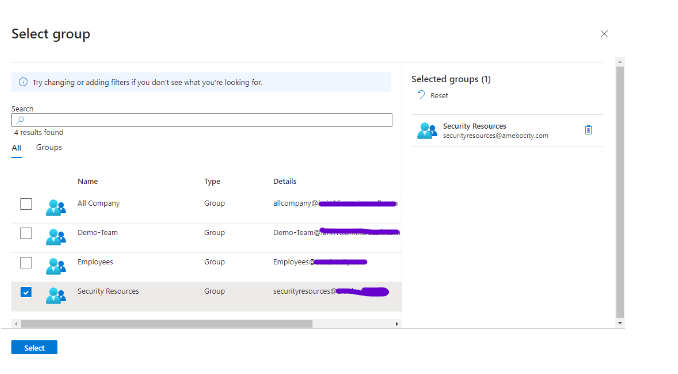
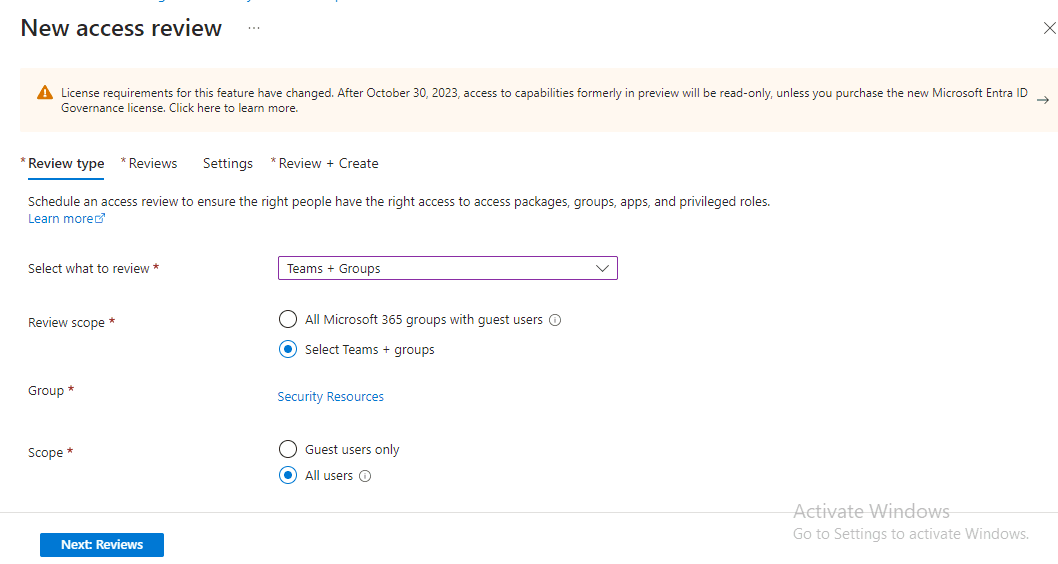
Step 2: Choosing Review Type and Scope I selected ‘Groups + Teams’ as the review type. I also selected ‘Select Teams + groups’ as the review scope and chose ‘Security Resources’. Then, I clicked ‘Select’. Next, I chose the scope as ‘All Users’ and clicked the ‘Next Review’ button to proceed to the next page.
Step 3: Defining Review Settings Under ‘Specify reviewers’, I selected ‘Manager of users’ as the primary reviewer, which is the IT Security Manager. Additionally, I selected Olusayo Joel, the Assistant IT Security Manager, as the fallback reviewer in case the primary manager is unavailable or on leave.
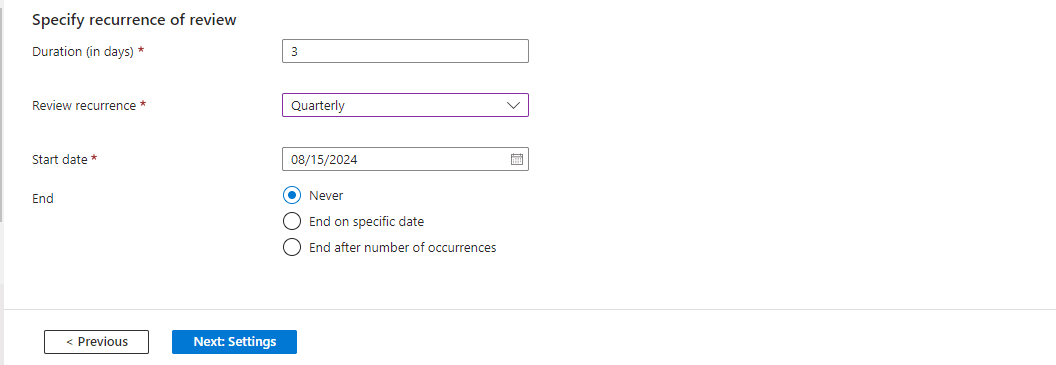
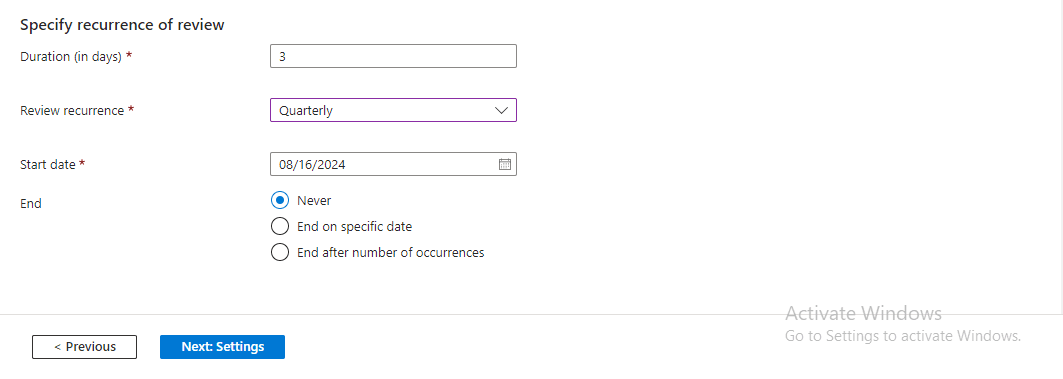
Under ‘Specify recurrence of review’, I entered 3 as the ‘Duration (in days)’, indicating the time period available to complete the access review. I also selected ‘Quarterly’ as the review recurrence to ensure that only authorized individuals have access to the Security Resources group. Furthermore, I set August 15, 2024, as the ‘Start Date’ and checked the ‘Never’ button as the end option, implying that the access review will continue to occur every quarter indefinitely.

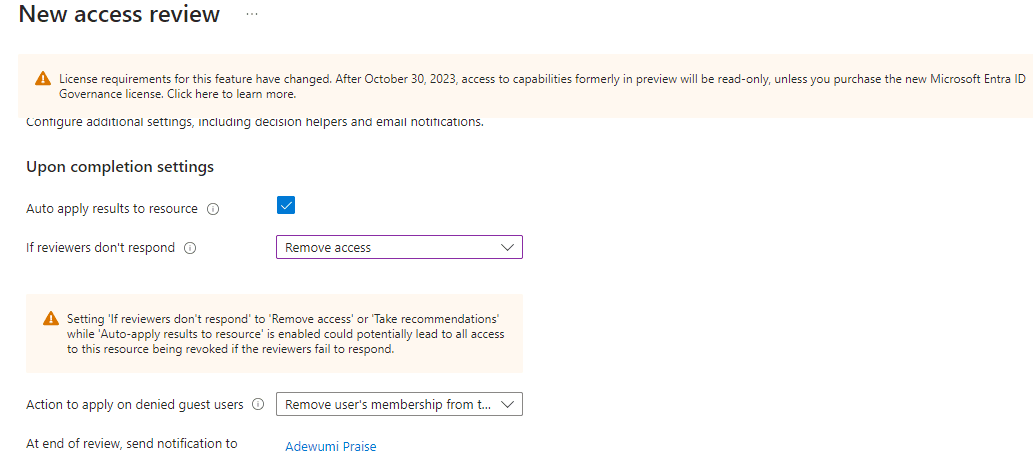
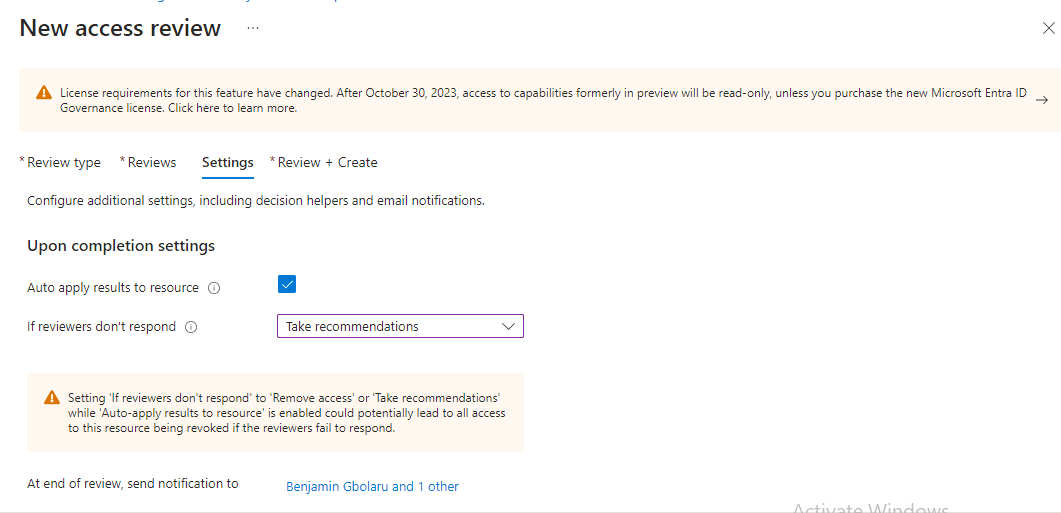
Under ‘Upon completion settings’, I checked the box for ‘Auto apply results to resource’. This means that if any user’s access is denied, their access to the resources will be removed automatically after the review is completed. I also selected ‘Remove Access’ as the action to take if reviewers don’t respond.
Additionally, I chose Adewumi Praise, the IT Manager, to receive notifications at the end of the review.
I checked the box for ‘No sign-in within 30 days’, as this is a crucial security consideration. If someone hasn’t signed in for 30 days, it poses a security risk that requires investigation.
I did not check the ‘User-to-Group Affiliation’ box, as it is not necessary for users to interact with each other to perform their duties.

Step 4: Configure Advanced Settings Under Advanced Settings, I checked the box for ‘Justification required’ to ensure that reviewers provide a justification for their decisions when denying or approving a user’s access.
I also checked the box for ‘Email Notification’ to enable Azure AD to send emails to reviewers when an access review starts, and to the review owner when a review is completed.
Furthermore, I checked the box for ‘Reminders’, which means that Azure AD will send reminder emails to all reviewers at the midpoint of the review period for in-progress access reviews.

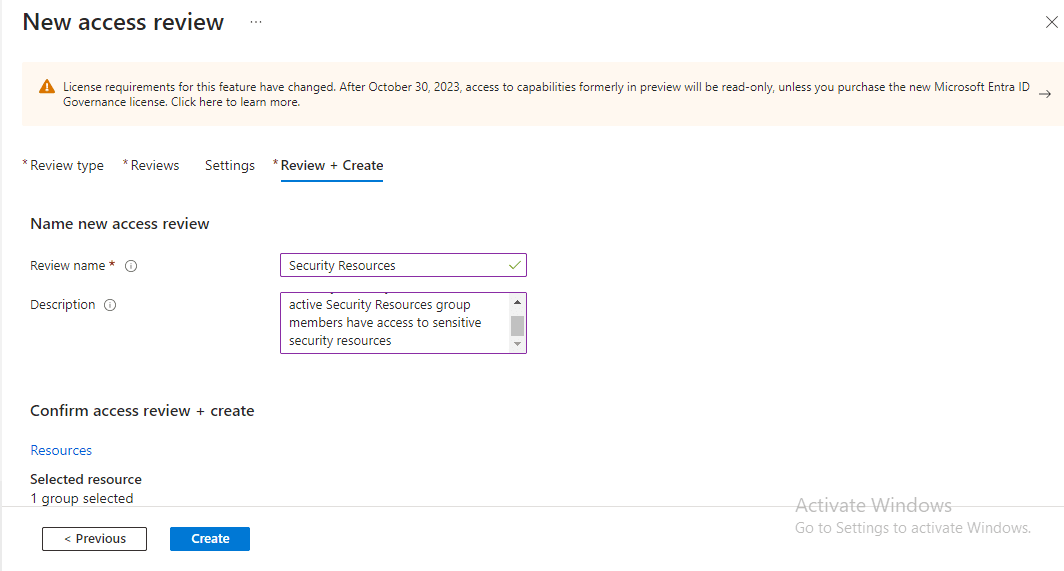
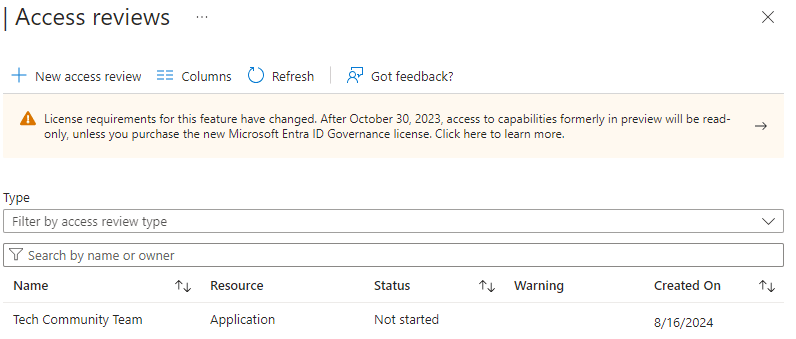
Step 5: Review and Create Policy Under ‘Review + Create’, I named the new Access Review as ‘Security Resources’ and entered a description. Then, I clicked on ‘Create’, initiating the commencement of reviewing users in the Security Resources group membership.
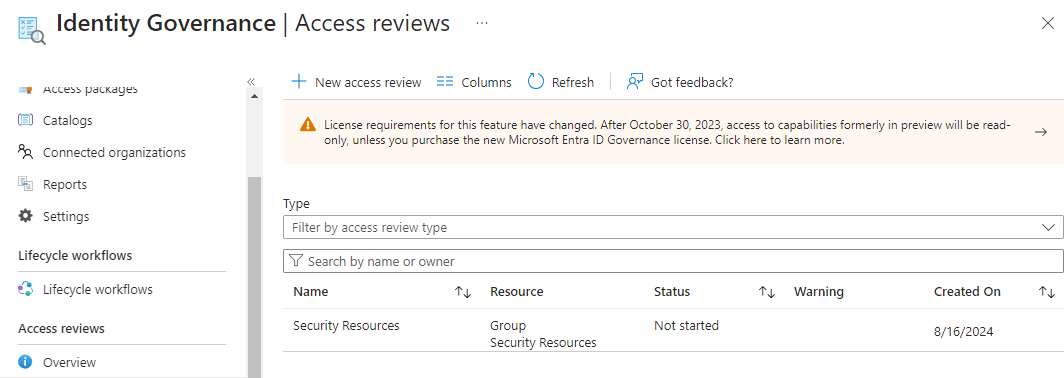
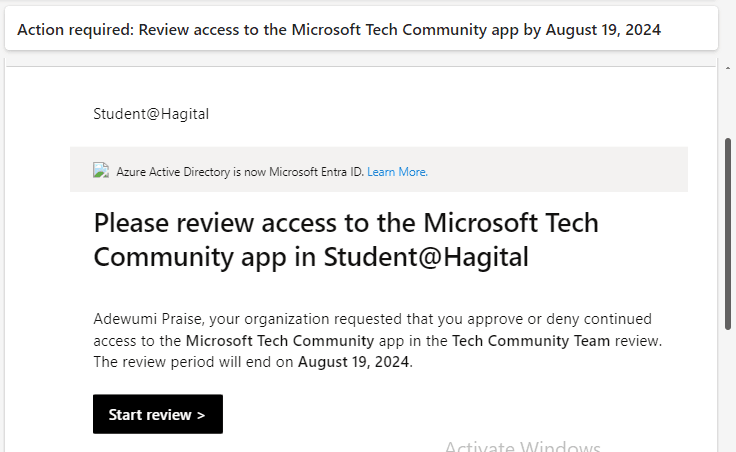
Step 6: Access Review Initiation To see how the review works, the manager of the users needs to log in to their Outlook email account (or log in to myaccess.microsoft.com) to commence the review. An email will appear in their inbox, and they should click the “Start Review” button to be redirected to ‘My Access’, where they will be prompted to approve or deny access to the members of the Security Resources group, as shown in the screenshot below.
That is exactly what I did, as I used Adewumi Praise’s account, the IT Security Manager, to implement the process. I logged in to his Outlook email account, clicked on the “Start Review” button, and followed the prompts to review and manage access to the Security Resources group.
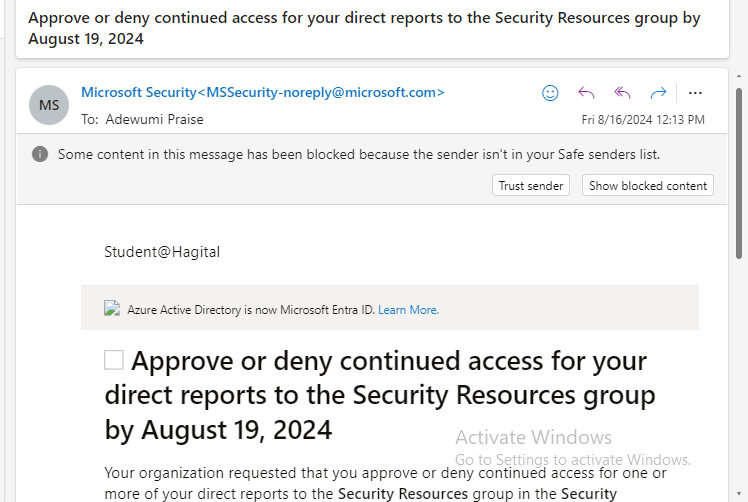
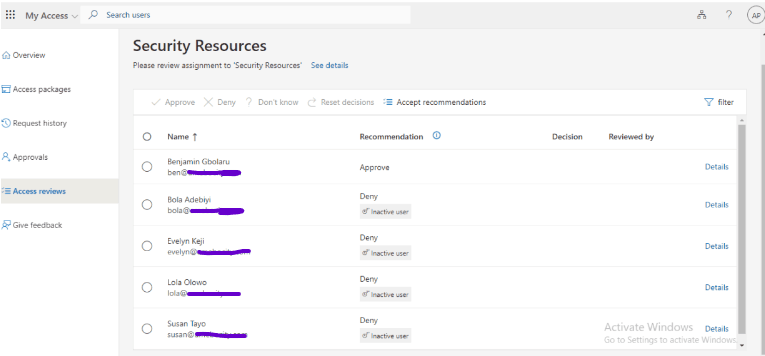
From the screenshot above, notice that only Benjamin Gbolaru is deserving of being approved, while others like Bola, Evelyn, Lola, and Susan are recommended to be denied due to their inactivity. The reason for this may be that they have been transferred to another department within the organization. Therefore, I will follow the recommendation.
Please note, as you read my report, that the example I’m using is purely hypothetical and for illustrative purposes only.
So, I approved only Benjamin with the reason that he is active in the group and still remains in the Security department within the organization. Meanwhile, I denied the rest (Bola, Evelyn, Lola, and Susan) with the reason that they have been transferred to another department within the organization, which is why they are no longer active in the group.
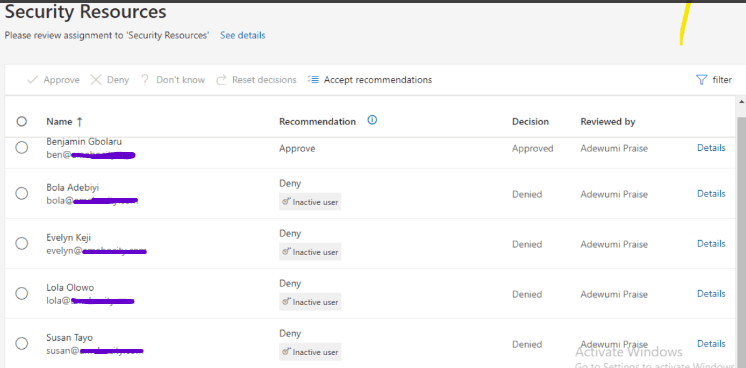
The screenshot below shows the Access Review details and illustrates how all the denied users were automatically removed from the Security Resources Group.
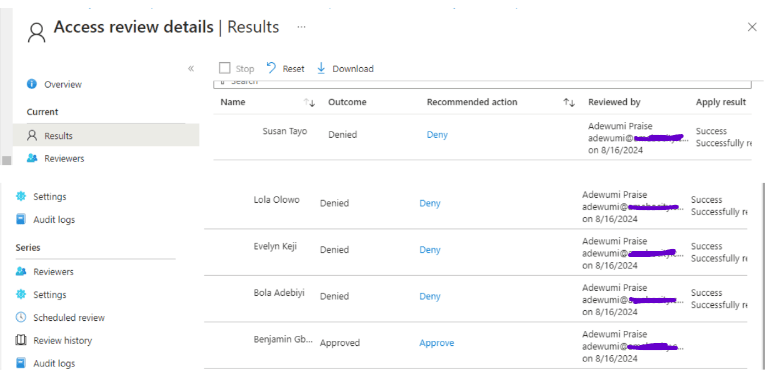

From the screenshot, you can see that only Benjamin remains in the group.
By following the 6 steps outlined above, I have successfully configured access reviews for Teams and Groups, ensuring regular verification of access privileges and maintaining a secure environment within the organization.
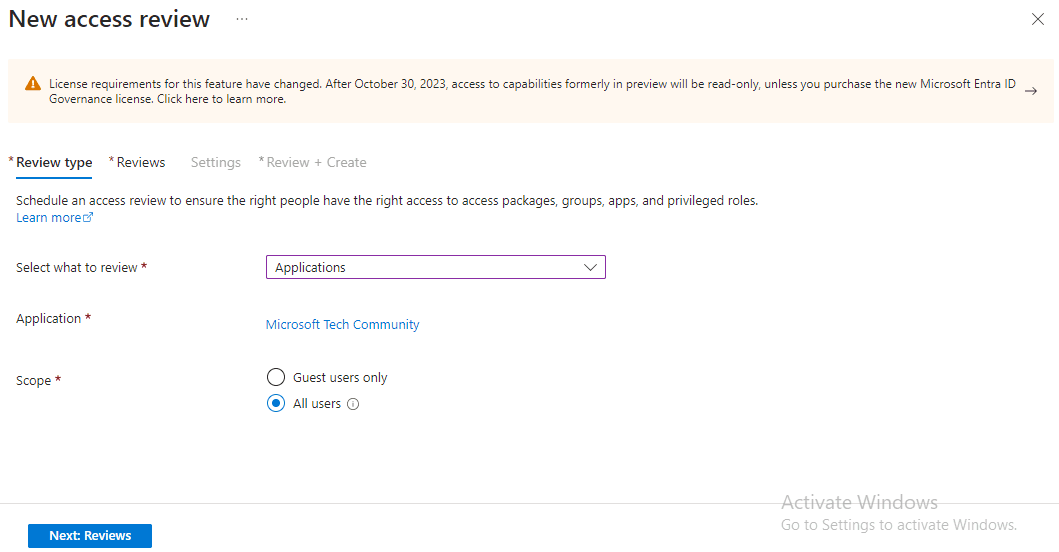
Access Review configuration is not limited to just Teams and Groups; it can also be applied to Applications. Let me show you how it can be done step by step with screenshots. To illustrate this, let’s imagine another scenario where the Microsoft Tech Community application requires regular access reviews to ensure that only active employees who are part of the Tech Community team have access.
To implement the scenario, I have completed some prerequisites by adding the Tech Community Team’s Group and two users outside of the group, Adenike and Amarachi, to the Microsoft Tech Community Application. I also checked using my account to see if I have access to the newly added app.
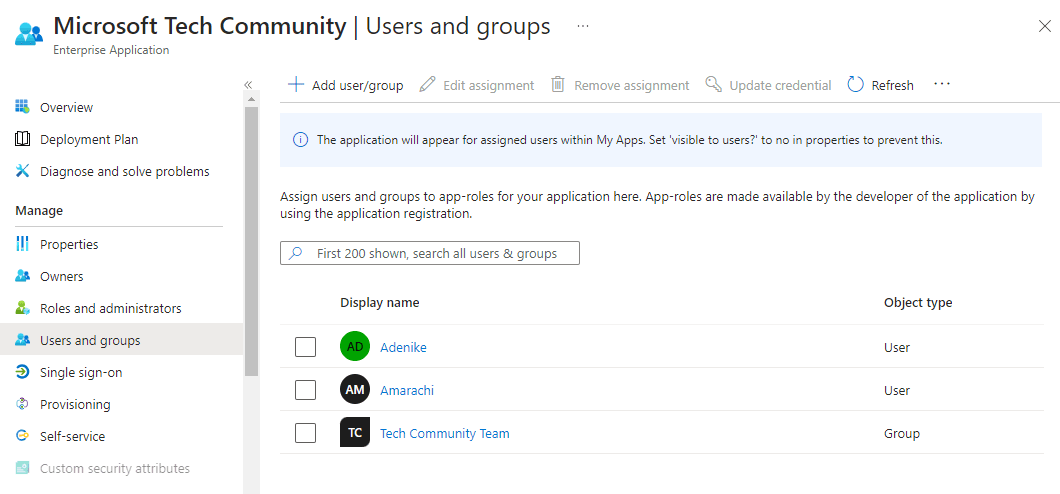
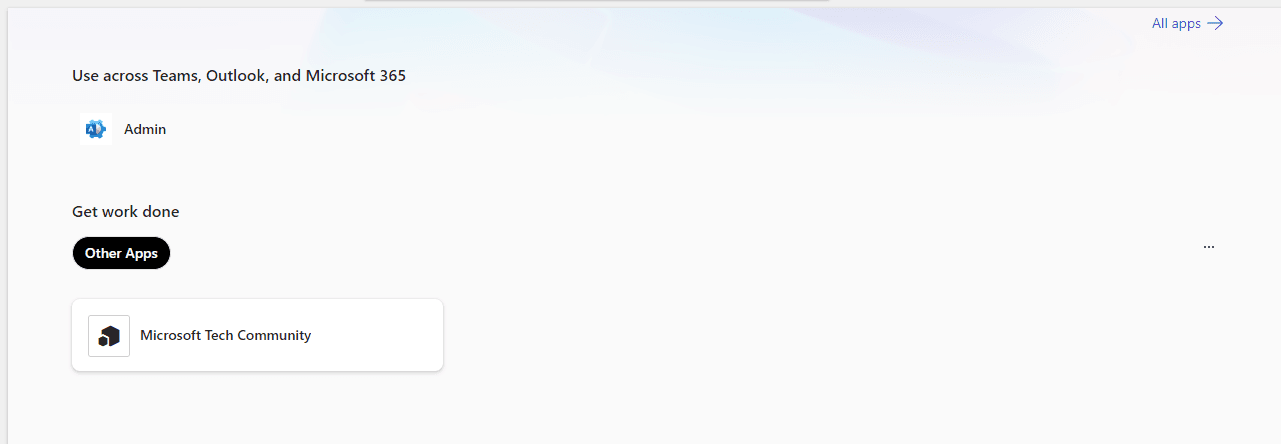
Steps:
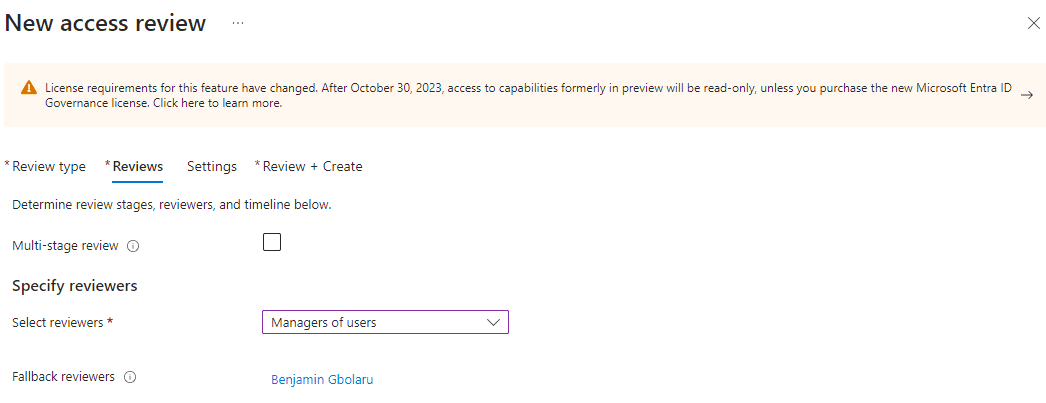


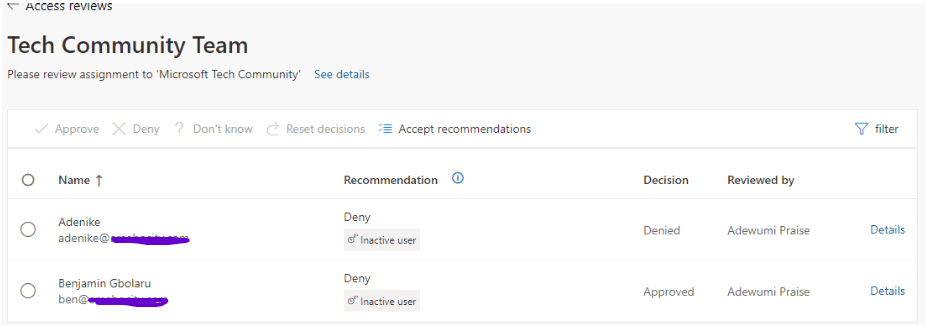
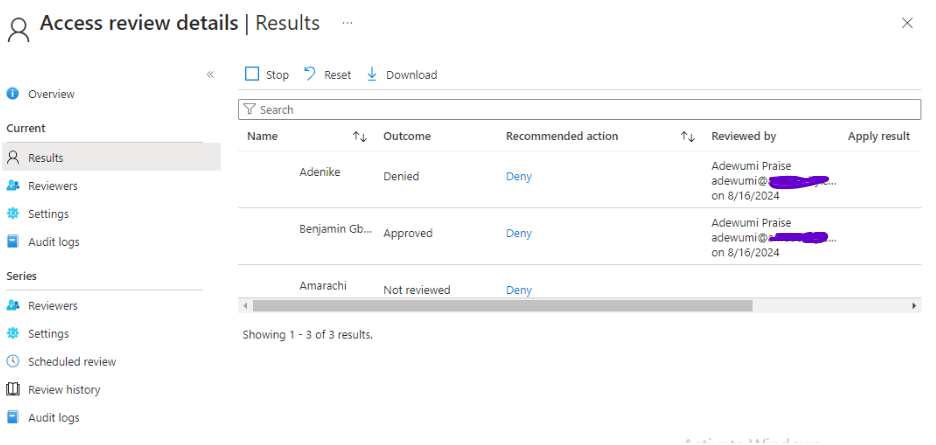
From the screenshot above, you will notice that Amarachi’s manager has not yet reviewed her access, and this can be done before the 3-day deadline elapses.
The Access Review for the Microsoft Tech Community application ensures that only authorized employees have access to sensitive information and resources, reducing the risk of unauthorized access and maintaining a secure environment within the organization.
Here are the top 10 best practices for effective access reviews, most of which I also use when configuring access reviews.
By following these best practices, organizations can ensure effective access reviews, maintaining security and compliance.
I have successfully described the benefits of Access Review, configured Access Review, and outlined best practices for effective Access Review.
An Administrative Unit in Microsoft Entra ID is a logical grouping of resources and users within an organization, used to delegate administration and manage access control.
Administrative Units delegate some of the power of Global Administrators for efficient management within an organization, especially if the organization is a global company with offices in every part of the world and thousands of users. Since Microsoft recommends a maximum of five Global Administrators, it would be challenging for them to manage numerous users alone, so there is a need to delegate their power.
Administrative Units are crucial for the efficient, secure, and compliant management of resources and access within an organization. Below are the seven benefits of Administrative Units in an organization:
Using a scenario where BenTech Ltd., a global company, wants to delegate administration of their African offices’ resources and access to a regional IT team. To achieve this, they need to create an Administrative Unit to manage users, groups, and resources specific to the African region. Here are the steps to implement this scenario in Administrative Units in Microsoft Entra ID:
Steps:
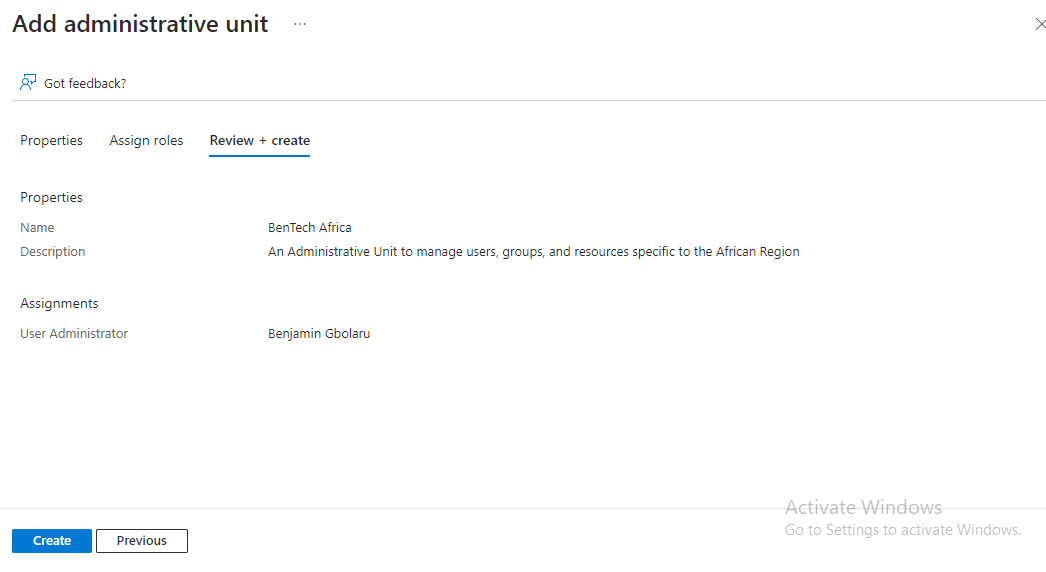
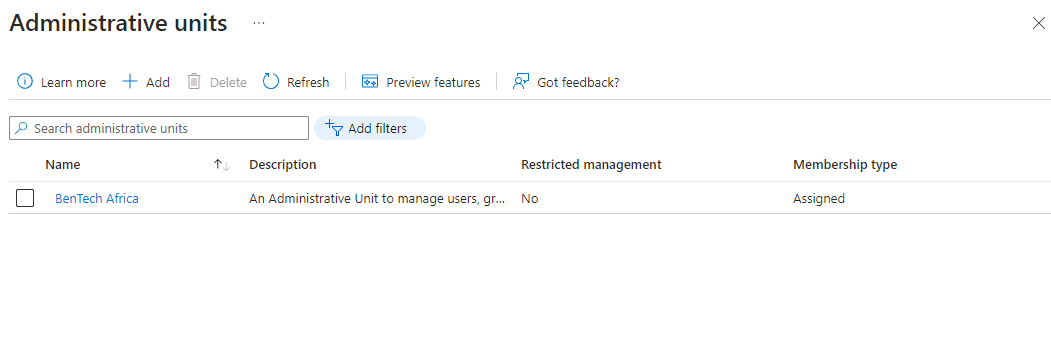
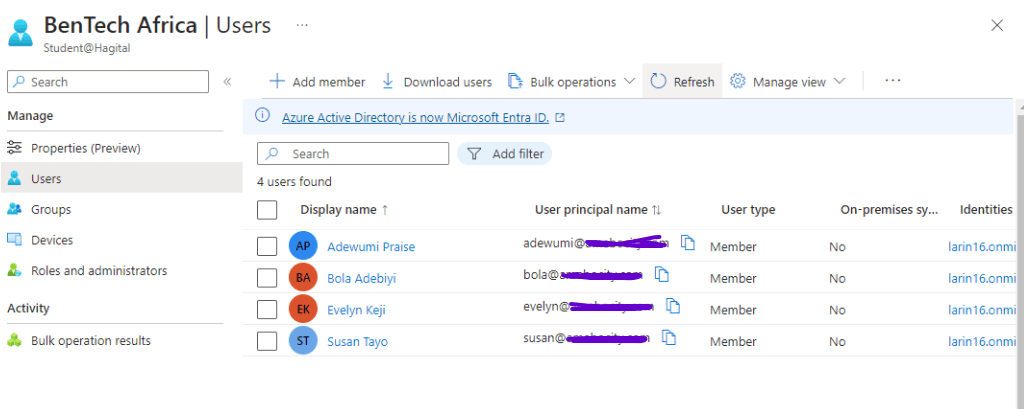
Whenever these members have issues, there won’t be any need to disturb the Global Administrator to resolve them; rather, the person with the User Administrator role in the BenTech Africa office will be the one to solve them.
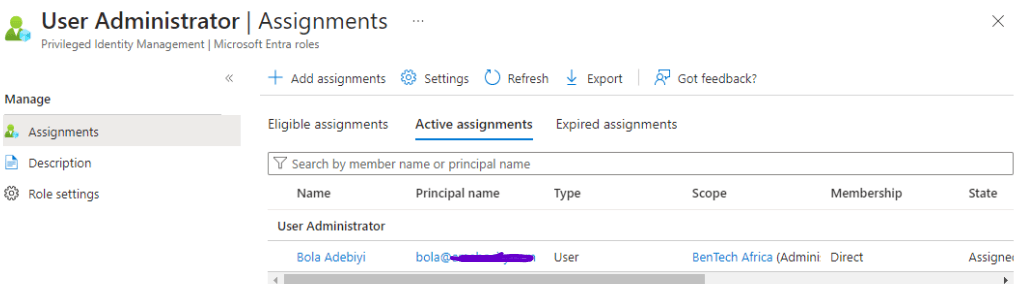
As shown in the screenshot above, you will notice that the scope is tied to the BenTech Africa Admin Unit, rather than the Directory (Tenant) level.
From the screenshot below, you will notice that Bola Adebiyi has access to only the users in the BenTech Africa Admin Unit, enabling him to perform his administrative role without access to the entire BenTech organization. This is why he cannot add members, as the option is greyed out. If there is a need for another user to join the BenTech Africa Admin Unit, the Global Admin will add the user. However, any other tasks involving the management of these users within the BenTech Africa Admin Unit will be handled by Bola Adebiyi, the IT Leader in BenTech Africa.
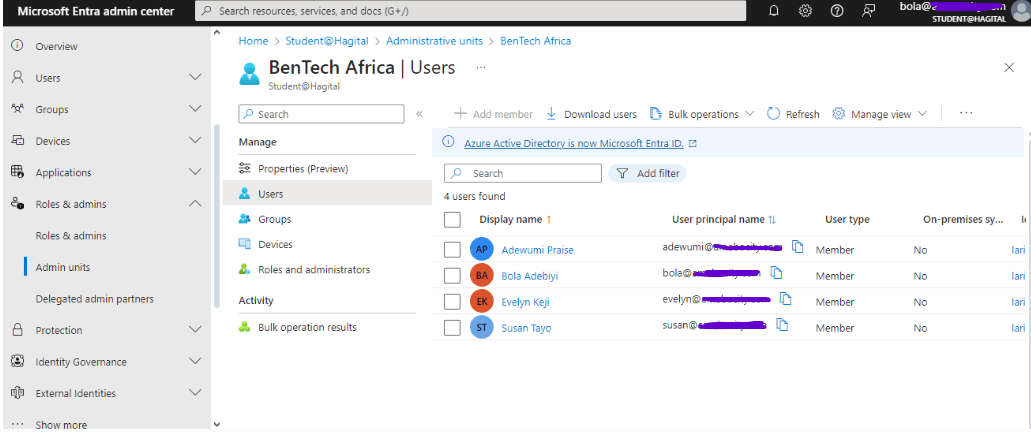
From the steps above, I have successfully configured an Admin Unit. Additionally, I have demonstrated, through a practical scenario, the importance of Admin Units for a global organization. Note that Access Reviews can be performed for an Admin Unit, as the members of the unit will be in a group. By using the step-by-step guide on how to configure access reviews that I stated earlier, this illustrates how the three topics I am reporting on can be used together to enhance security and compliance in an organization.
Administrative Units are a key feature for managing access and governance in an organization. Use these 10 best practices to ensure an efficient framework that meets your organization’s needs.
With my explanation, I have provided a clear and insightful overview of the benefits of Administrative Units. I have also demonstrated the configuration of an Admin Unit using a scenario and outlined 10 best practices for the effective management of Admin Units.
Privileged Identity Management (PIM) is a Microsoft Entra ID service that helps you manage and secure access to sensitive resources in your organization. This includes resources in Microsoft Entra ID, Azure, Microsoft 365, and other Microsoft online services.
In a nutshell, what PIM helps to achieve is to manage what users with privileged roles (such as Global Admin, Billing Admin, User Admin, and so on) can do in an organization or within a tenant.
Here are the top 4 benefits of Privileged Identity Management that help protect an organization’s sensitive resources:
To configure PIM in an organization, there are steps to follow. I will use the following scenario to practically configure PIM: BenTech Company has hired two new contractors, Adewumi and Bola, to work as Administrators for a 3-month contract period. Adewumi will be working as a User Administrator, while Bola will be working as a Security Administrator. To ensure that their access to sensitive resources is limited to the duration of their contract and that their privileges are properly managed, BenTech Organization Policy requires me as a Global Administrator to apply Privileged Identity Management (PIM) to both Adewumi and Bola.
Step 1: Signing Into Entra ID Admin Center
Step 2: Add Adewumi and Bola to PIM
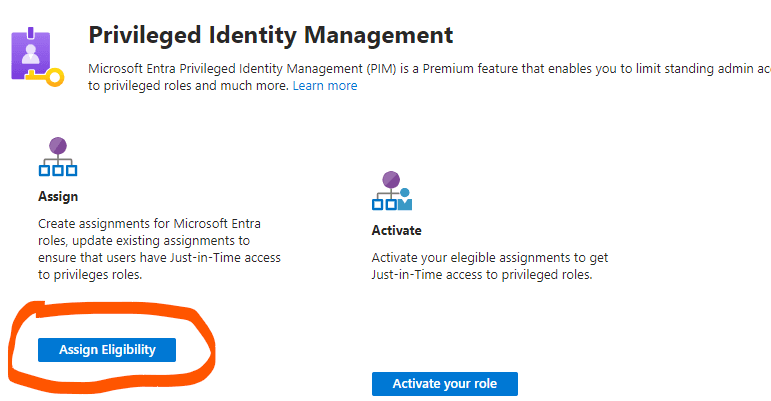
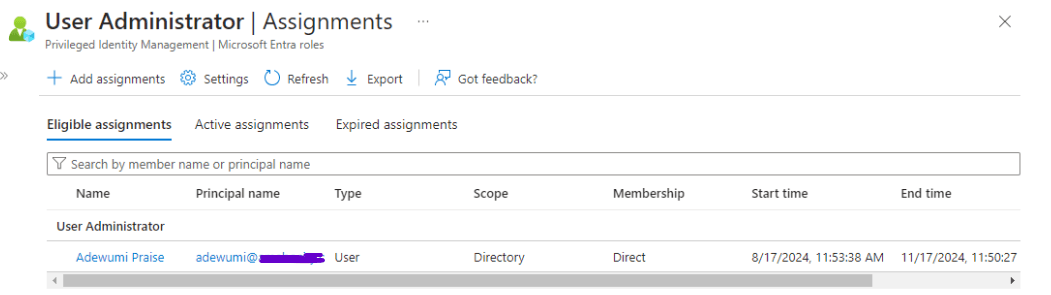
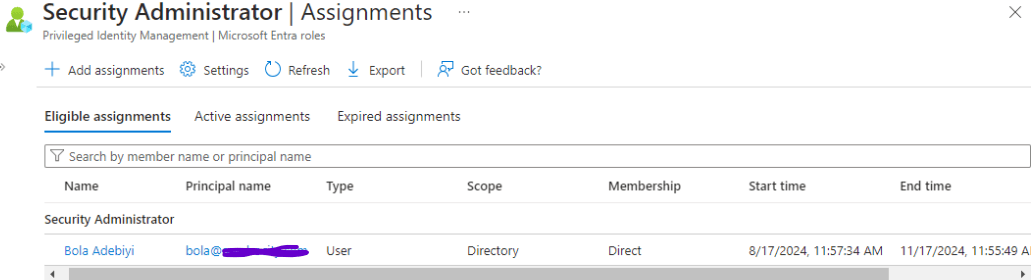
Under PIM, I clicked on “Microsoft Entra roles”, then clicked on “Assign eligibility”. I chose the “User Administrator” role and assigned Adewumi to it. I also selected the “Security Administrator” role and assigned Bola to it.
Step 3: Configure Role Settings
I went to “Role settings”, selected “User Administrator” and “Security Administrator”, and configured the following settings:
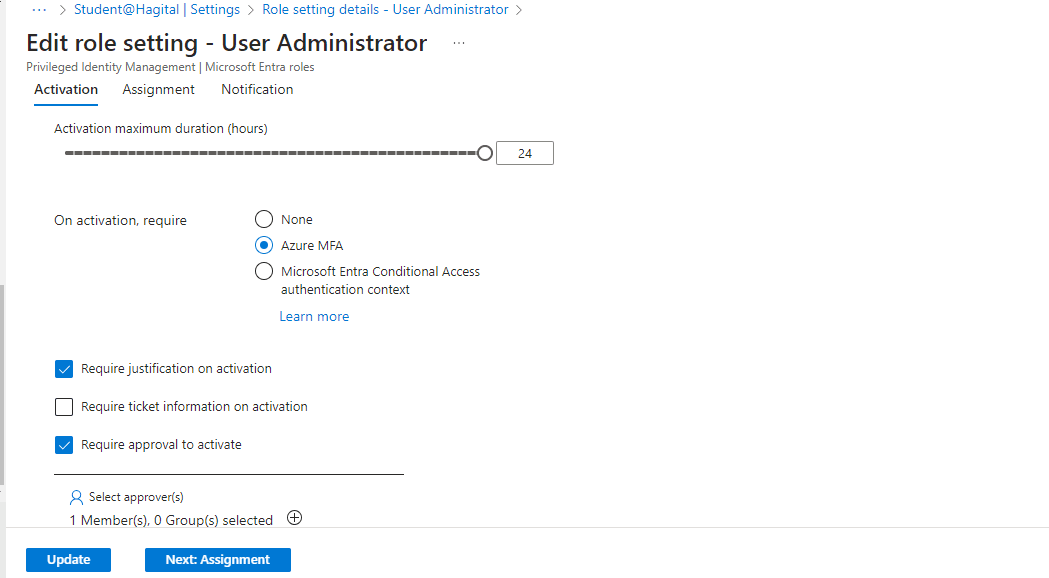
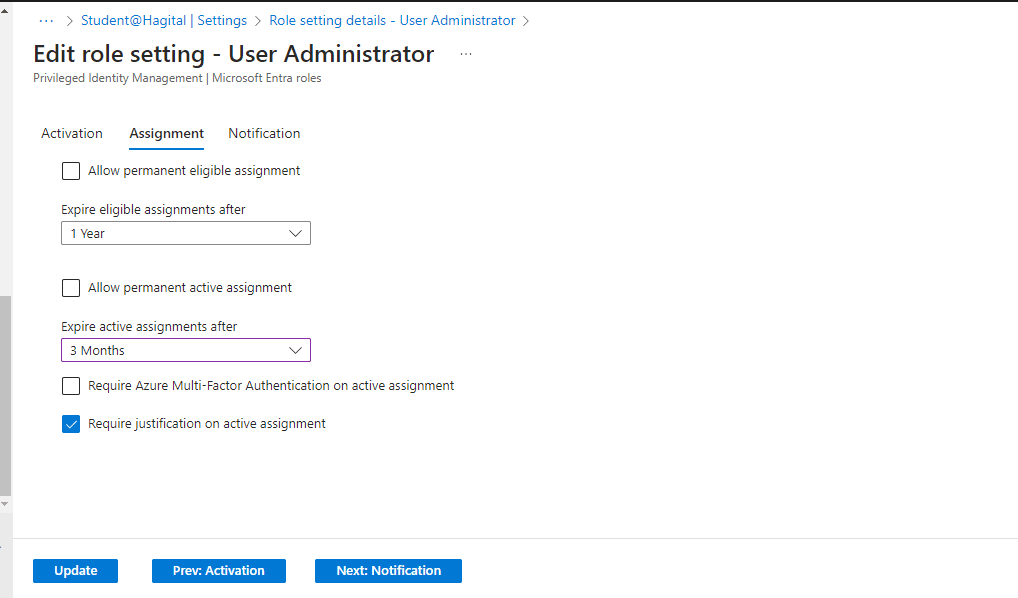
I then configured the following additional settings for the User Administrator role:
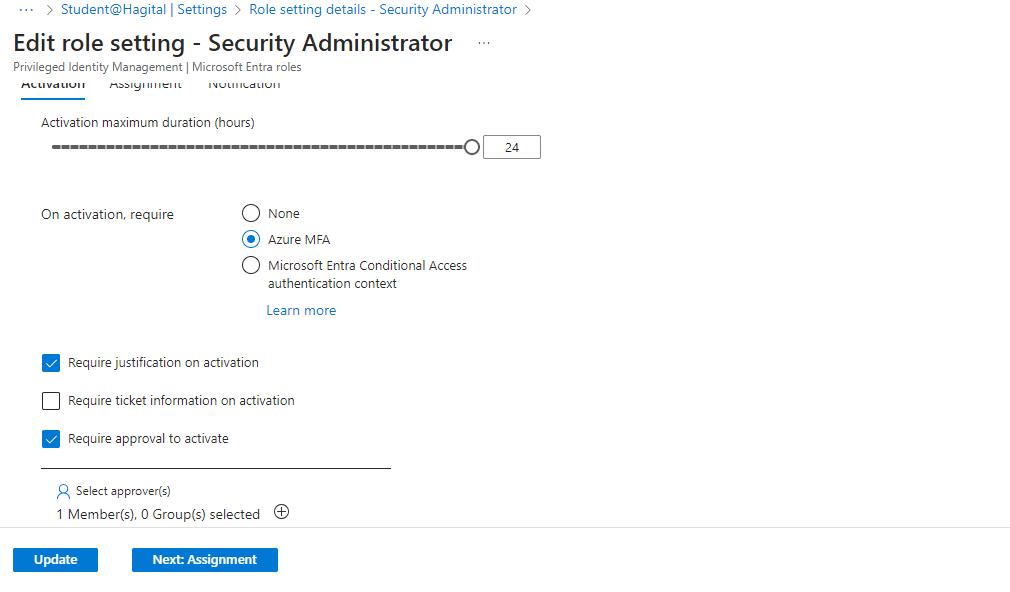
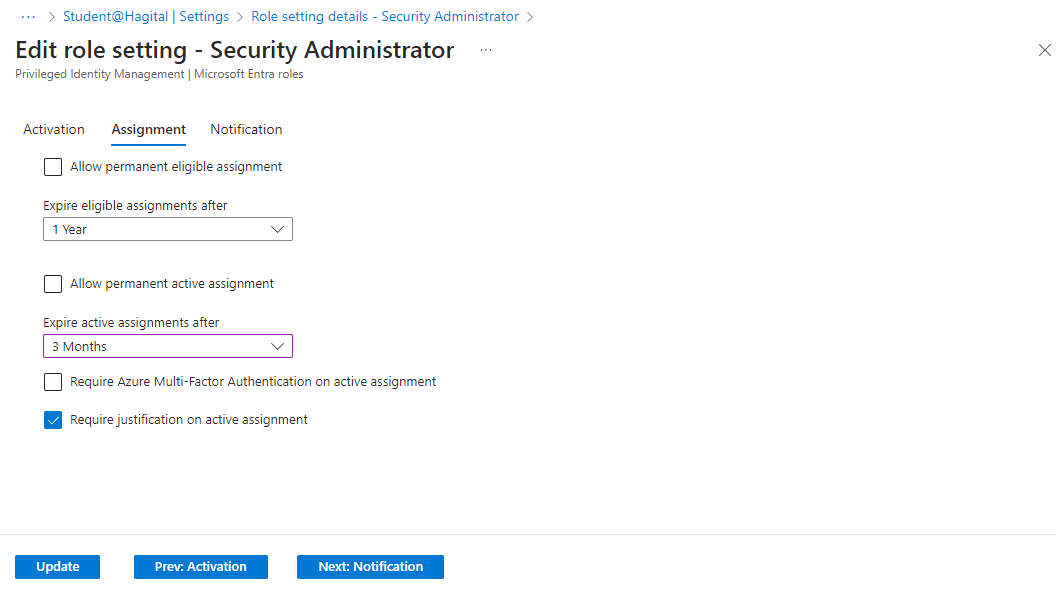
I applied the same edit process to the Security Administrator role as I did for the User Administrator role, configuring the identical settings as shown in the screenshots below.
Step 4: Adewumi and Bola log in to their respective Entra ID accounts to activate their assigned roles.
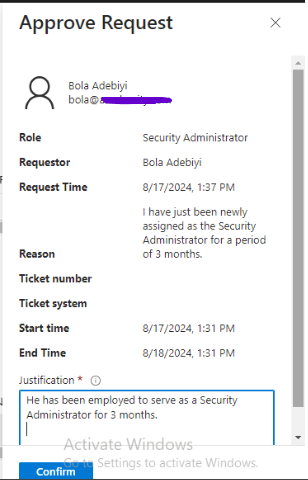
Bola clicks on the “Activate” button and provides a reason: “I have just been newly assigned as the Security Administrator for a period of 3 months.”

I then log in to the Entra Admin Center to approve Bola’s activation request.
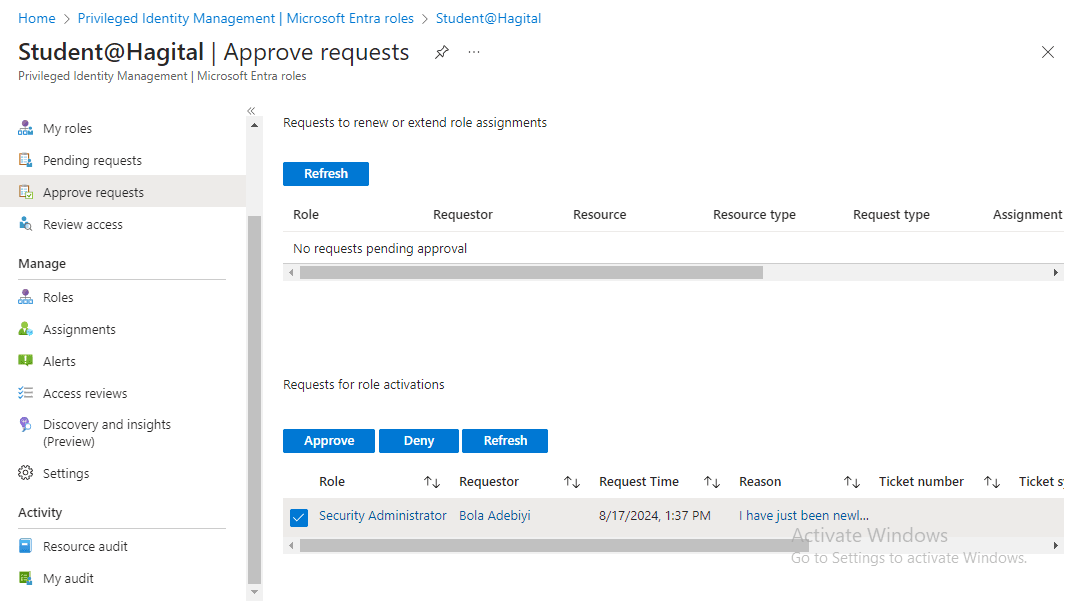
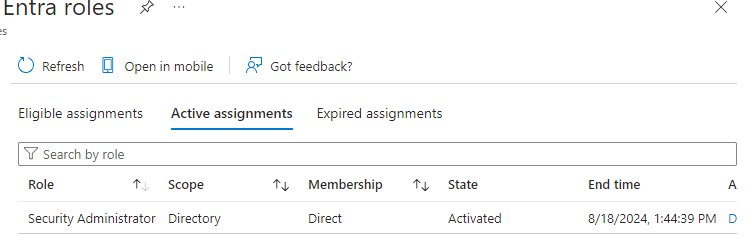
Bola’s role as a Security Administrator is activated.
Adewumi also clicks on the “Activate” button and provides a reason: “I have just been newly assigned as the User Administrator for a period of 3 months.”
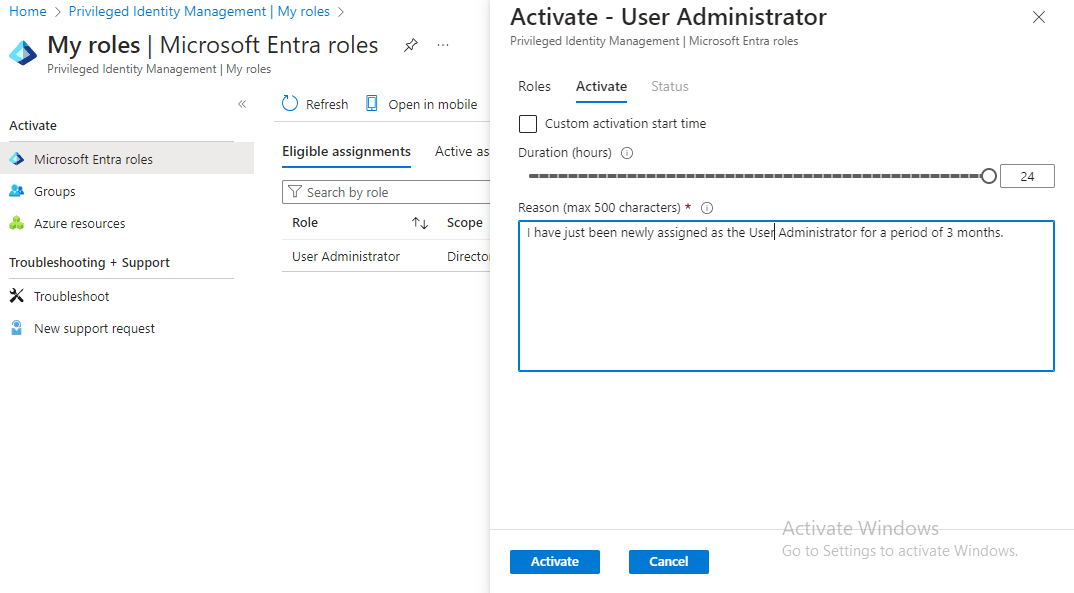
I then log in to the Entra Admin Center to approve Adewumi’s activation request.
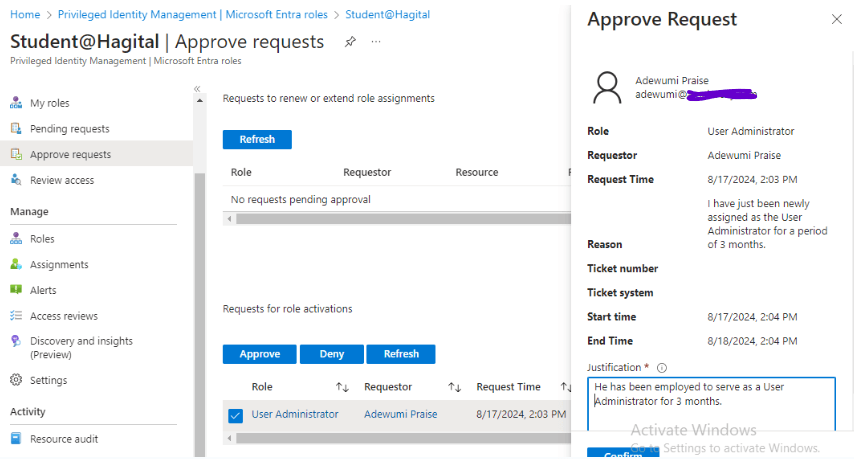
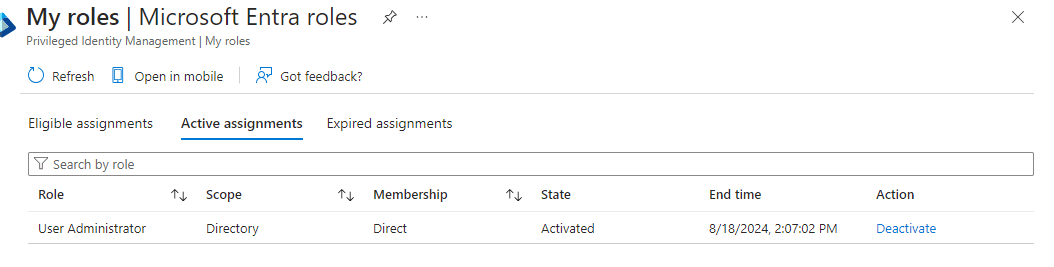
Adewumi’s role as a User Administrator is activated.
Step 5: Configure Access Reviews
To configure Access Reviews in PIM, on the PIM page, I click on “Microsoft Entra roles”, then I click on “Access reviews”. I then select the most critical privileged roles, such as Global Administrator, User Administrator, Security Administrator, and Global Reader, to review.
To initiate the Access Review in PIM, I configured the following settings:
In the Advanced settings, I enabled:
With these settings in place, I clicked ‘Start’ to initiate the Access Review process. See Screenshot Below.
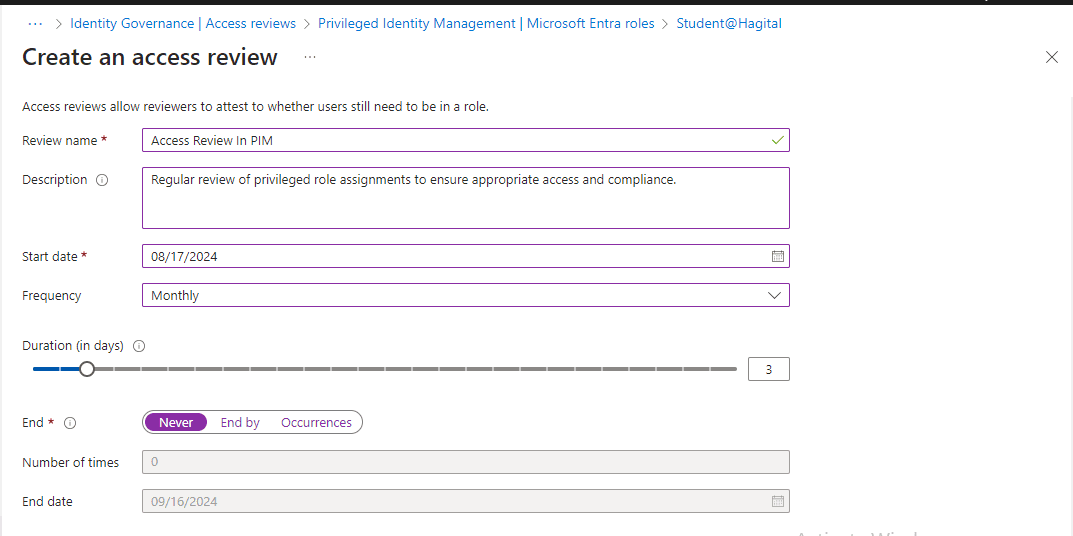
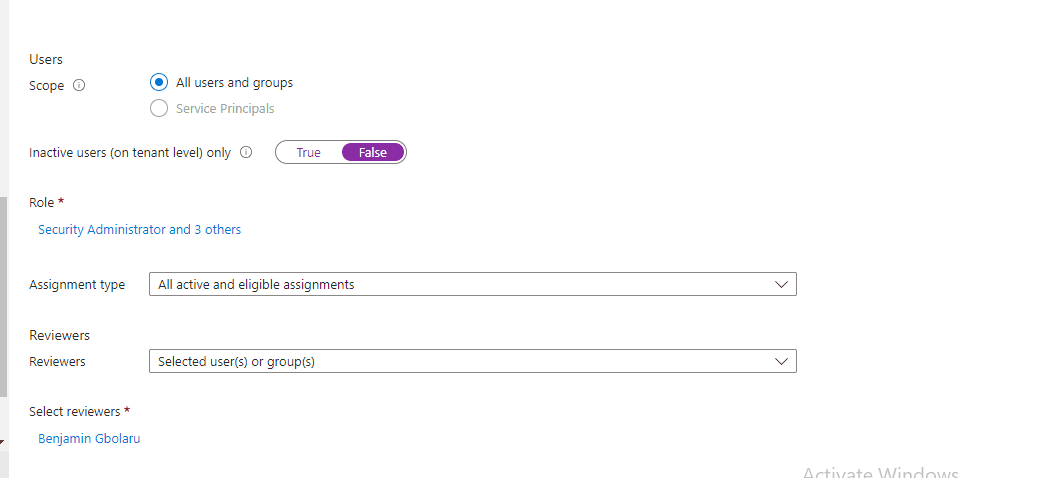
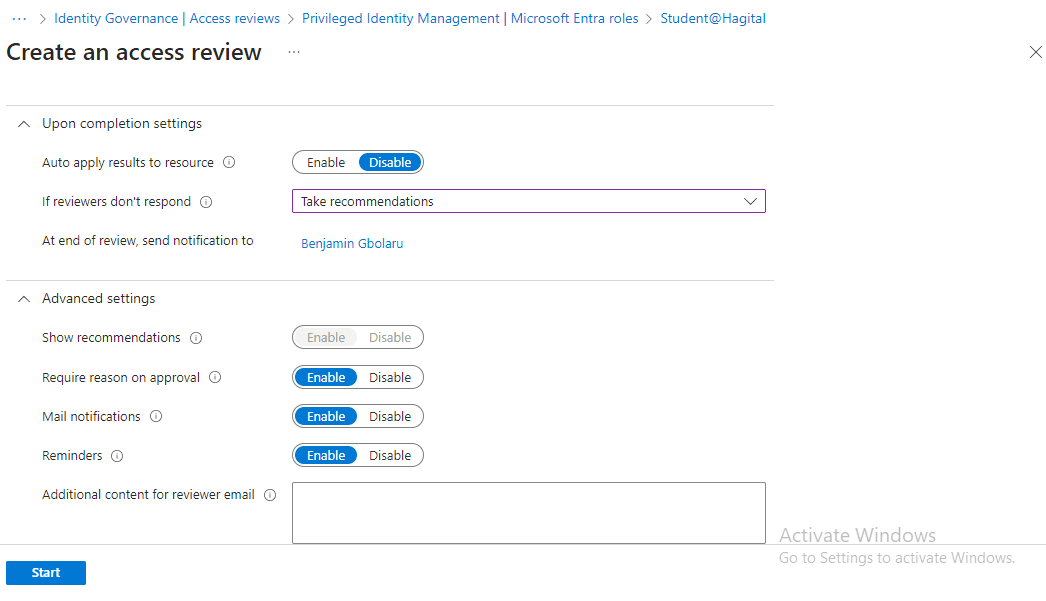
Step 6: Initiating Access Review
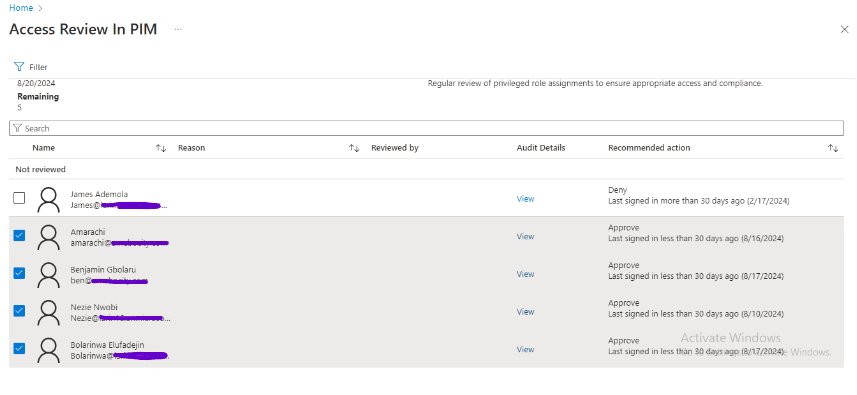
I log in to my Outlook email account and receive an email requesting me to review access to the Security Administrator, User Administrator, and Global Administrator roles. To commence the review, I click on the “Start Review” button.
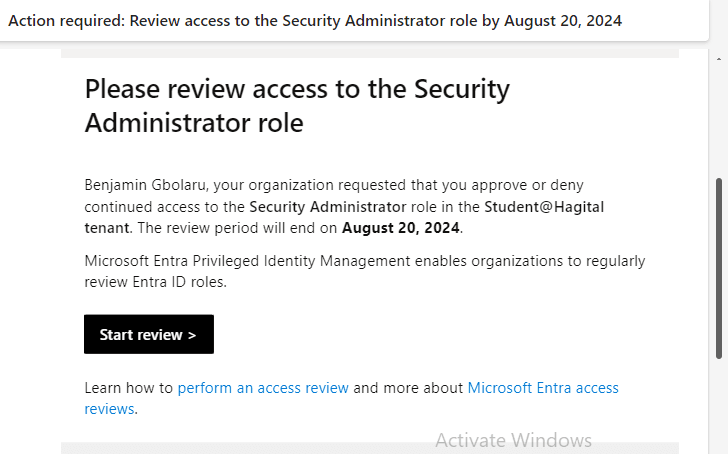
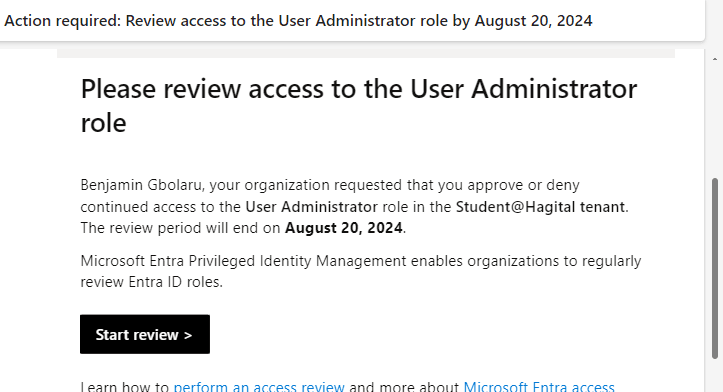
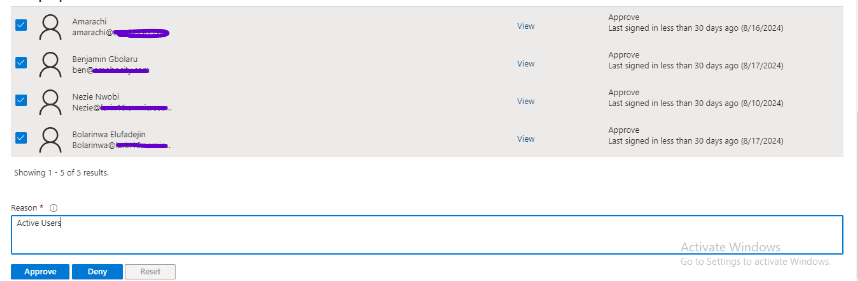
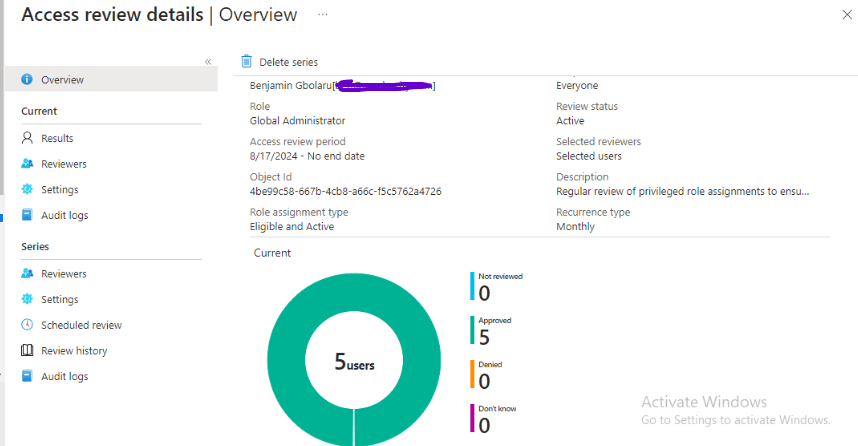
I review Bola’s access as a Security Administrator and follow the recommendation to approve his access.
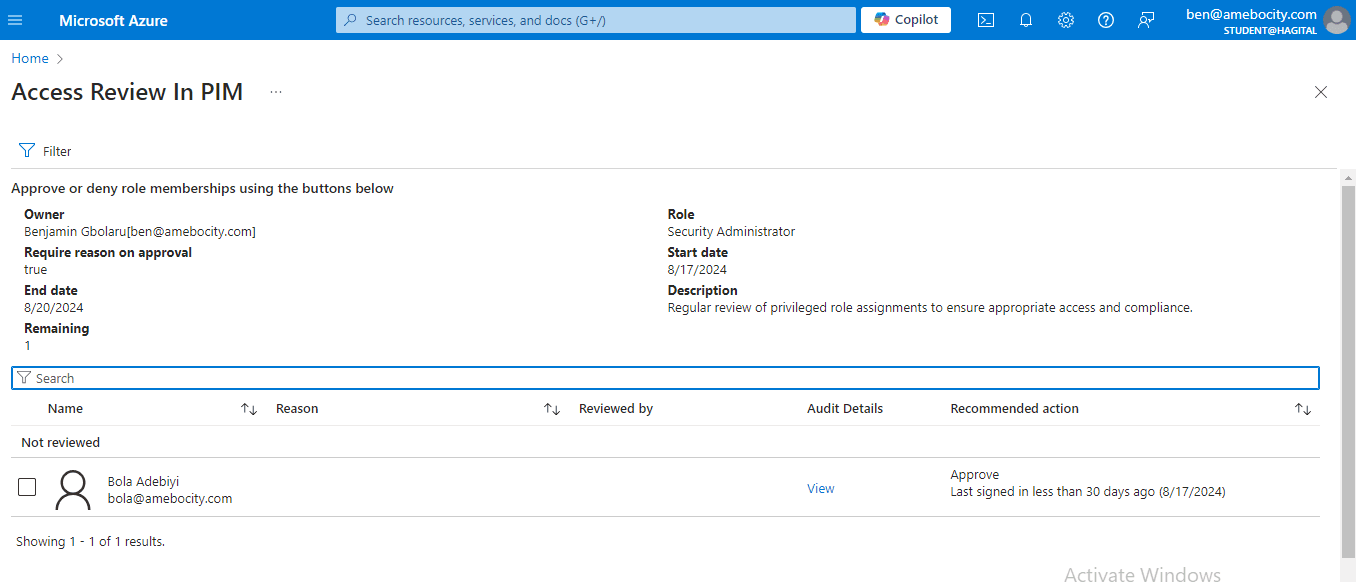
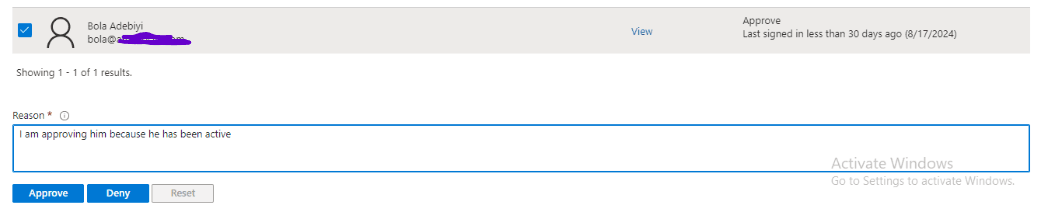
I also review Adewumi’s access as a User Administrator and follow the recommendation to approve his access.
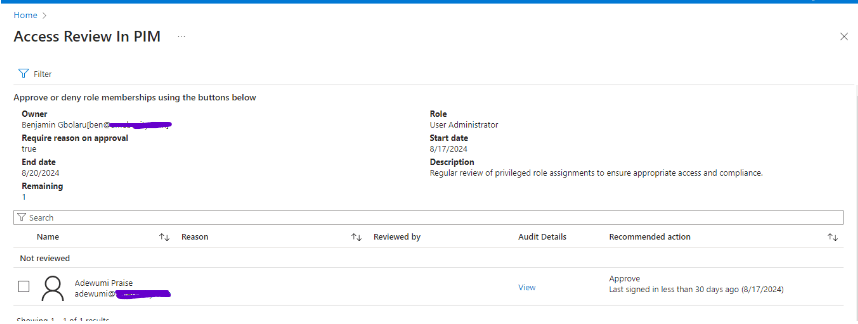
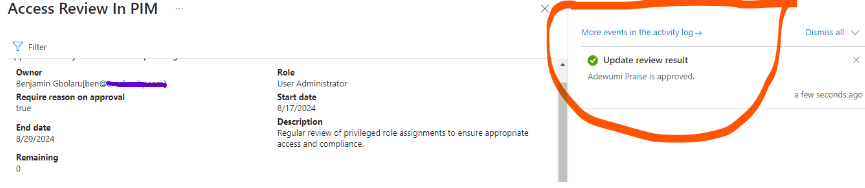
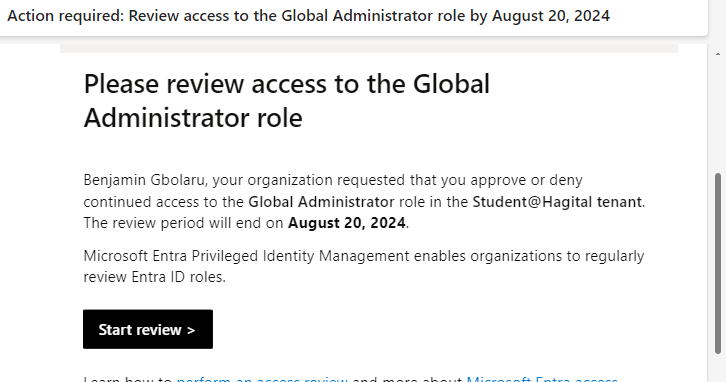
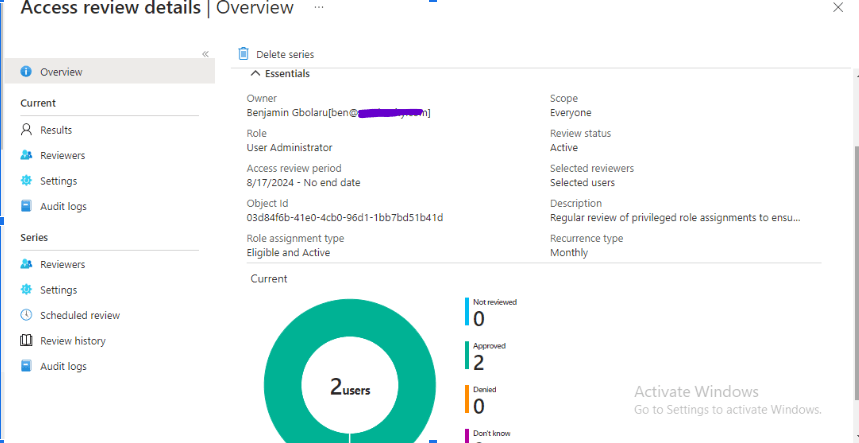
The screenshot below shows how I reviewed access for the Global Administrator role, although it was not part of the initial scenario. However, there are users with the Global Administrator role that require review.
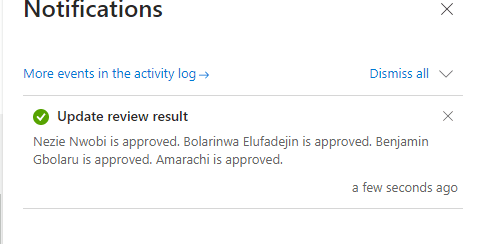
I successfully created an Access Review, initiated the review process, and completed it.
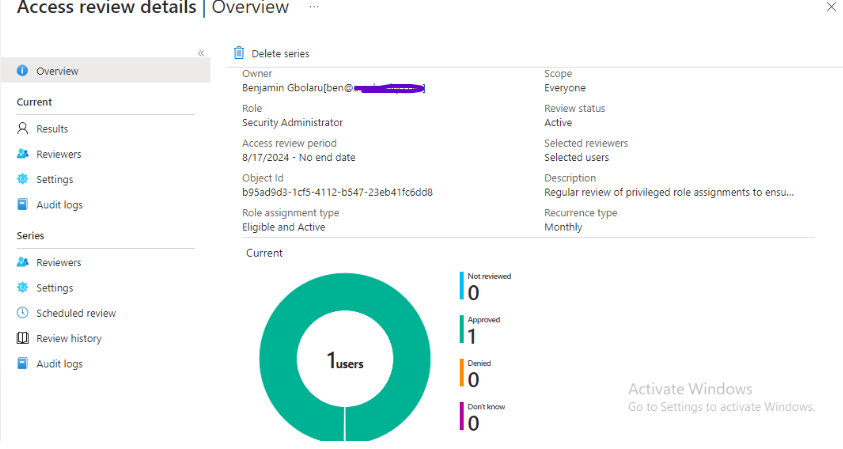
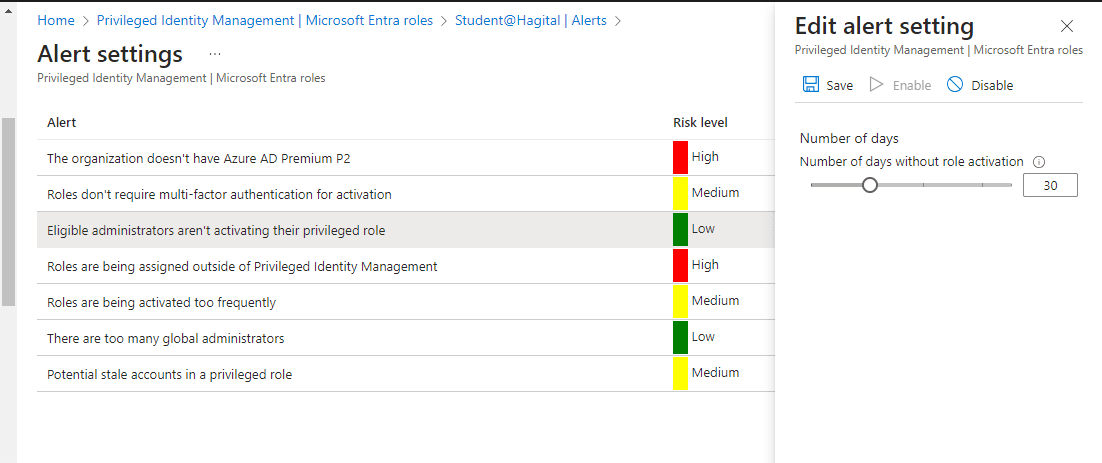
Step 7: Configure Alerts
Inside PIM, I set up necessary alerts in order to stay aware of any potential security risks.
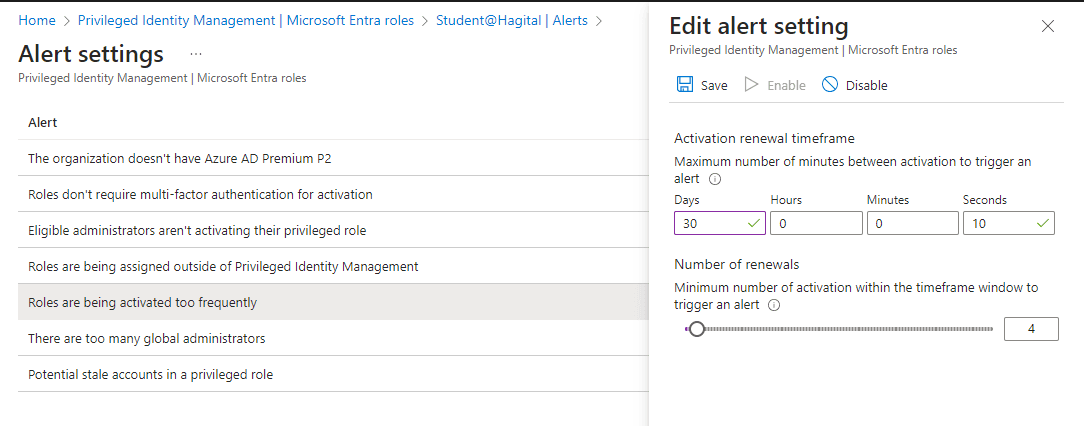
By following these steps, BenTech Organization can ensure that Adewumi, Bola, and other users’ access to privileged roles is secure, limited, and monitored, and that their privileges are revoked automatically at the end of their contract period.
Here are the top 8 best practices for effective Privileged Identity Management (PIM):
By following these top 8 best practices, organizations can effectively manage privileged identities, reduce security risks, and protect sensitive data.
In this report, I have successfully explained the meaning of Privileged Identity Management (PIM) and its advantages. Additionally, I have demonstrated a practical configuration of PIM using a real-world scenario and outlined 8 essential best practices for effective PIM implementation.
I strongly recommend that every organization implements and utilizes Access Reviews, Administrative Units (Admin Units), and Privileged Identity Management (PIM). By doing so, they can:
Implementing these measures will:
By adopting these practices, organizations can significantly enhance their security posture, optimize operations, and maintain a secure and compliant environment.
In my report, I have successfully demonstrated the best way to implement Access Reviews, Admin Units, and Privileged Identity Management (PIM) with Microsoft Entra ID. I have provided their benefits, used different scenarios for configurations, stated best practices, and provided recommendations. This report shows that Access Reviews, Admin Units, and PIM are important Entra ID features for effective identity management. By implementing and configuring these features effectively, organizations can significantly enhance their security posture, reduce risk, and improve compliance.
Need expert assistance with Microsoft Entra ID features? Contact Medha Cloud today!
Our team of certified professionals is ready to help your organization configure and optimize Access Reviews, Admin Units, and PIM to strengthen security and ensure compliance. Let Medha Cloud guide you in leveraging these powerful tools in Microsoft Entra ID for effective identity management and a robust security posture.

