What is user lifecycle management (ULM)?

Imagine you run a business with 100 employees. You use over 30 different software solutions, some on-premises, others SaaS. You hire new employees, promote some, and sometimes people leave the company.
You also add new software to make your processes more efficient. But every time someone joins or leaves, or their role changes, managing their access takes a week, causing missed deadlines and unhappy users. Sound familiar? User Lifecycle Management (ULM) is here to help.
ULM helps ensure users have the right access at the right time, from the day they join to the day they leave. By using ULM, companies can improve security, make IT processes smoother, and keep users happy.
Key takeaways
- User Lifecycle Management oversees a user's journey from onboarding to offboarding.
- Effective ULM enhances security by controlling access to sensitive information.
- Automation in ULM saves time and reduces errors in user management.
- Monitoring user behavior helps identify potential security risks.
- Personalizing user experiences can improve engagement and satisfaction
Introduction
User Lifecycle Management (ULM) is a structured approach to managing users from the moment they join until they leave the organization. Think about how much time and effort goes into creating accounts, assigning access, changing permissions, and eventually removing access. ULM streamlines this process, ensuring your users are productive and secure, which helps avoid downtime and boosts satisfaction.
What is user lifecycle management ULM?
User Lifecycle Management (ULM) is the process of managing user accounts and access throughout an employee's time at your company. It starts when users are onboarded, continues through their active engagement, and ends with offboarding. The goal of ULM is to make sure users have appropriate access when needed, and that access is updated or removed as circumstances change. By managing user access well, ULM ensures security, efficiency, and a better user experience.
Importance of ULM for businesses
Think about how often employees join, leave, or change roles in your company. Without ULM, each of these situations can lead to inefficiencies, security risks, and dissatisfaction. Here’s how ULM makes a difference:
Security
- ULM ensures that only authorized people have access to important information, helping protect sensitive data.
- Role-Based Access Control (RBAC) is used to give users the right permissions based on their roles, ensuring the right people have access to the right tools.
Efficiency
- Automated ULM processes reduce manual tasks for IT teams, speeding up onboarding and offboarding, so new hires can get started without delay.
- By automating repetitive tasks, IT can focus on more strategic activities that drive value.
Compliance
- ULM helps companies meet data protection regulations like GDPR and HIPAA by ensuring access is always up-to-date.
- Proper access control and record-keeping help your company stay compliant with data protection rules and avoid penalties.
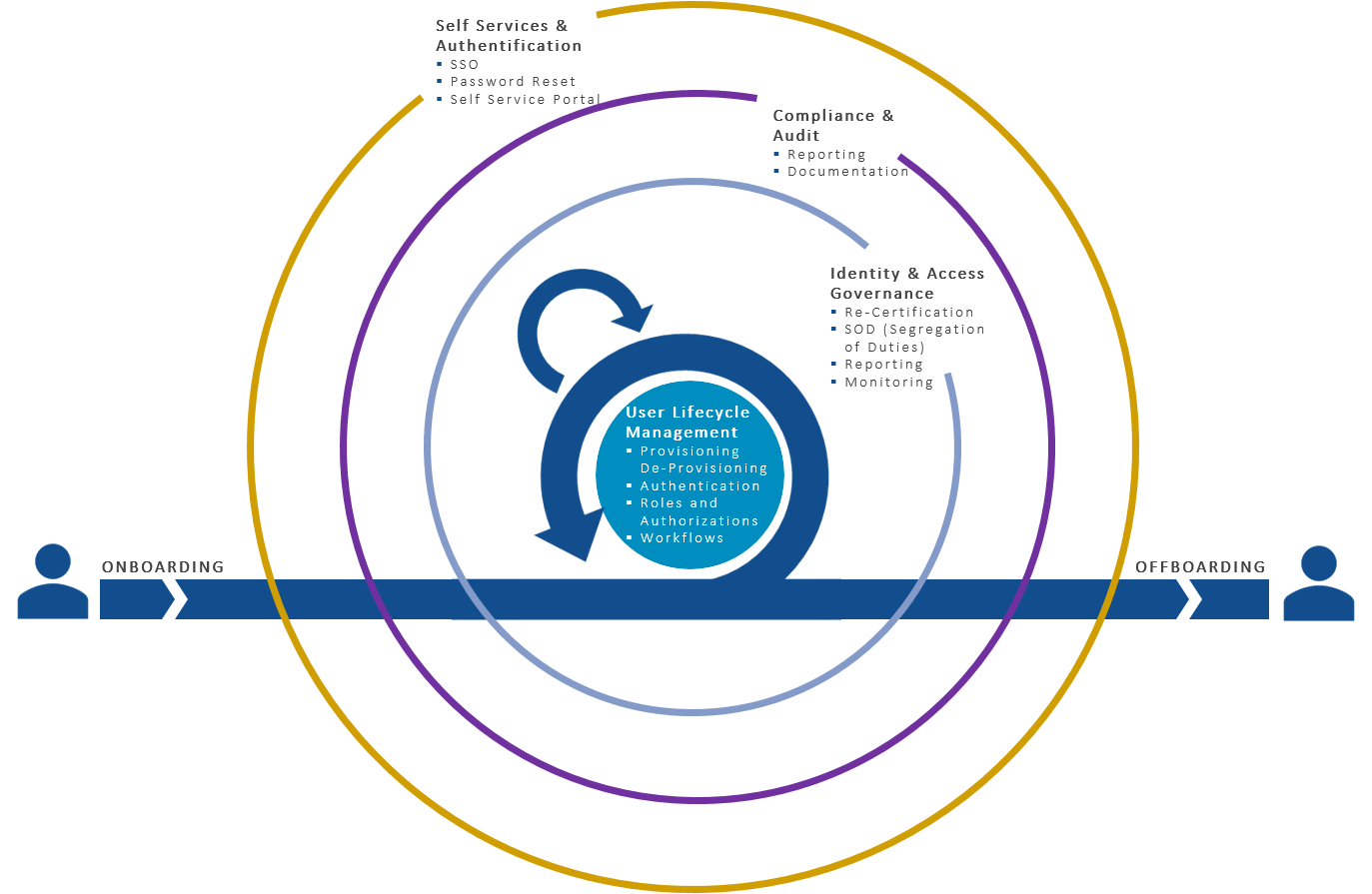
Key stages of ULM
Effective User Lifecycle Management (ULM) involves managing users through different stages of their journey within an organization. Here are the key stages that ensure users have the appropriate access while minimizing security risks:
Onboarding: Setting up new users effectively
Onboarding is the first stage of the user lifecycle. This involves setting up accounts, assigning appropriate permissions, and provisioning all necessary tools to new users on their first day. A smooth onboarding process ensures users can start contributing immediately, boosting morale and productivity.
Struggling with onboarding delays? Consult Medha Cloud for a seamless User Lifecycle Management implementation. We provide the best possible solutions at the lowest cost with a quick turnaround
>>>> Talk to us – We’re available on Live Chat <<<<
Engagement: Keeping users informed and engaged
Engagement involves keeping users connected to the organization's tools, resources, and communications. It includes ensuring users have access to necessary information, training resources, and company updates. Regular engagement helps users feel informed, motivated, and aligned with company goals.
Retention: Strategies to keep users happy and reduce turnover
Retention focuses on keeping users satisfied with their access and resources over time. It involves regularly reviewing permissions to ensure users have what they need to do their jobs effectively and personalizing their experience to enhance productivity. A well-managed retention process reduces frustration and turnover, contributing to overall user satisfaction.
Offboarding: Removing access securely when users leave
Offboarding is the final stage of ULM. It involves removing access to all systems, tools, and data when users leave the organization. Secure and timely offboarding is crucial to prevent unauthorized access and safeguard sensitive information. Effective offboarding ensures that the transition is smooth and secure, minimizing any potential risks to the company.
Practical scenarios in ULM
Managing the user lifecycle is not just about theory; it’s about solving everyday challenges that businesses face. Here, we'll explore three key scenarios: a new user joining, a user being promoted, and a user leaving. We will look at these situations from the perspectives of HR, system administrators, employees, and business owners.
New employee joins the company
Situation: A new hire is joining the company, and they need everything ready to start working immediately. The business owner wants productivity without delay, the HR department wants a smooth onboarding, the system admin needs to handle technical aspects, and the new employee wants to feel welcomed and equipped.
Without ULM
- HR Perspective: HR manually fills out onboarding forms, requests software licenses, and coordinates with IT to create accounts and assign permissions. This process can take days and often involves back-and-forth communication.
- System Administrator: The system admin manually creates accounts in Active Directory, adds the user to appropriate groups, assigns licenses, and installs software on their devices. This manual effort is time-consuming and prone to errors.
- Employee Experience: The new hire might have to wait several days before gaining access to all the tools they need, leading to frustration and a delayed start.
- Business Owner's View: The business owner sees a delay in productivity, with new hires spending valuable time waiting for access instead of contributing to projects.
With ULM process
- HR Perspective: HR simply fills out a digital form with the new employee's information. Based on the role provided, the ULM system automatically triggers account creation, assigns the right group memberships, requests the necessary software access, and initiates software installation with minimal HR intervention.
- System Administrator: The system admin relies on ULM to automate most of the tasks. The ULM system sets up accounts in Active Directory, adds the user to appropriate groups, assigns licenses, and installs required software on their devices, including both on-premises and SaaS tools. The system admin only needs to oversee the process and handle exceptions, saving valuable time.
- Employee Experience: The new hire receives all the necessary credentials and access on day one. They can access email, collaborative tools, and specific software without having to wait, which makes them feel productive from the start. They fill out a self-service onboarding form, which helps speed up the process and ensures they have all the tools they need.
- Business Owner's View: The business owner sees immediate productivity and no wasted time. A well-implemented ULM system ensures all this happens with minimal manual intervention. By automating the onboarding process, the business owner can trust that new hires are ready to contribute right away, without delays or disruptions.
Want to see how inefficient onboarding impacts productivity and employee morale?
Employee gets promoted
Situation: An existing employee has been promoted, and their responsibilities have changed. They need new access while some of their previous permissions need to be revoked. The employee wants the transition to be seamless, HR wants to ensure the new role is properly set up, and IT wants to ensure that security is maintained.
Without ULM
- HR Perspective: HR manually informs IT about the promotion and provides details for the new role. This process often involves multiple emails and follow-ups, which can cause delays.
- System Administrator: The system admin manually updates the user’s access, assigns new permissions, adds them to new groups, and removes old permissions. This manual process is prone to mistakes, such as overlooking certain permissions that should be revoked.
- Employee Experience: The promoted employee might face delays in getting access to the new tools and may still have access to resources they no longer need, leading to confusion.
- Business Owner's View: The business owner is concerned about the potential security risks of having outdated access still active and the delay in the employee’s ability to fully transition to their new role.
With ULM
- HR Perspective: HR updates the employee’s role in the system, and the ULM system automatically adjusts access permissions. This includes installing new software and removing access to unnecessary tools based on the updated role, ensuring the promoted employee gets everything they need without manual follow-up.
- System Administrator: The ULM system automates the process of updating group memberships, assigning new software, and revoking unnecessary permissions. The system admin only oversees the changes, which reduces errors and saves time.
- Employee Experience: The promoted employee can seamlessly start their new role with all the necessary software and resources, without delays. They feel empowered by having the right tools immediately.
- Business Owner's View: The business owner sees that employees can transition smoothly into their new roles without productivity loss. Security remains intact as old access is removed promptly, reducing the risk of unauthorized access.
Curious about how a lack of automation can derail an employee's smooth transition into a new role?
Employee leaves the company
Situation: An employee is leaving the company. The business owner wants to ensure data security, HR wants a smooth exit, IT wants to revoke all access, and the employee wants to leave without any issues.
Without ULM
- HR Perspective: HR manually notifies IT about the employee's last working day. This manual process can lead to delays, and sometimes access is not revoked in a timely manner.
- System Administrator: The system admin manually disables accounts, removes the user from groups, and uninstalls software from the user's devices. There is a risk of missing some accounts or permissions, leading to potential security gaps.
- Employee Experience: The departing employee may still have access to certain resources during their notice period, which can lead to unauthorized data access if not properly managed.
- Business Owner's View: The business owner worries about data security and potential unauthorized access, as manually revoking all permissions can lead to errors or delays.
With ULM
- HR Perspective: HR initiates the offboarding process through a ULM system, which automatically notifies IT and begins the account deactivation process. This ensures a smooth and timely exit for the employee.
- System Administrator: The ULM system automates the revocation of access, disabling of accounts, removal from all groups, and uninstallation of software from the user's devices. It also ensures that any important data is archived securely.
- Employee Experience: The departing employee’s access is removed smoothly without any unexpected interruptions during their final days. They can finish their tasks and hand over responsibilities effectively, knowing everything is handled systematically.
- Business Owner's View: The business owner can be confident that no sensitive data is left accessible to someone who no longer works at the company. ULM ensures all access is revoked promptly and securely, reducing security risks and maintaining data integrity.
Wondering how failing to remove access can lead to severe financial and reputational damage?
Best practices for effective ULM
Automate processes
- Automate tasks like onboarding, offboarding, and role changes to reduce human error and save time.
- Use tools like Azure Active Directory or SailPoint for automated processes, making sure everyone has the right access from day one.
Personalize employee experience
- Customize dashboards and tools based on roles so users get what they need without the clutter.
- Use multiple communication channels, such as email, chat, and push notifications, to keep users informed and engaged effectively.
Continuous monitoring and review
- Regularly monitor user activities to identify risks and ensure compliance.
- Periodically review access permissions, especially after role changes, to adjust as needed
Tools and technologies for ULM
User Lifecycle Management (ULM) involves the use of various tools and technologies to manage user access effectively, maintain security, and ensure compliance throughout an employee’s journey in the organization. Here are some key tools and technologies, along with their definitions and examples:
Identity and access management (IAM) solutions
What is IAM?
Identity and Access Management (IAM) refers to a framework of policies and technologies that ensure the right users have the right access to technology resources. IAM tools help manage digital identities, roles, and permissions, ensuring secure access to resources.
Examples:
- Microsoft Entra: Provides identity management by allowing organizations to manage users' digital identities, assign access rights, and enforce security policies effectively.
- Okta: A cloud-based IAM tool that offers single sign-on (SSO) and multi-factor authentication to secure access to applications and resources.
>>> Discover what IAM solutions are and how they can enhance security in your organization <<<
2. User provisioning tools
What is user provisioning?
User provisioning refers to the process of creating, managing, and maintaining users’ access rights to different resources within an organization. Provisioning tools automate the process of onboarding, updating roles, and offboarding users.
Examples:
- SailPoint: Automates user account setup and management by assigning appropriate access based on roles and ensuring compliance with organizational policies.
- JumpCloud: A cloud-based directory that helps centralize the management of user identities and access permissions, simplifying the provisioning and deprovisioning processes.
Single sign-on (SSO) solutions
What is SSO?
Single Sign-On (SSO) allows users to access multiple applications with one set of login credentials. This enhances the user experience by reducing password fatigue and improves security by centralizing authentication.
Examples:
- OneLogin: An SSO solution that provides secure access to numerous business applications, simplifying login processes while maintaining security.
- Okta: Allows users to sign in once and access multiple applications securely, providing a seamless experience across different tools.
>>> Learn what Single Sign-On (SSO) is and how it can benefit your organization
Monitoring and analytics tools
What are monitoring and analytics tools?
Monitoring and analytics tools help track user activities, identify unusual behavior, and provide insights into how resources are being accessed. These tools play a crucial role in ensuring security and compliance, enabling proactive measures to prevent potential breaches.
Examples:
- Splunk: Provides real-time monitoring and analytics, helping track user activities, detect suspicious behavior, and respond to potential security incidents.
- SolarWinds: Monitors user access patterns, generates detailed reports, and provides alerts to ensure compliance with security standards.
5. Endpoint management tools
What is endpoint management?
Endpoint management involves managing and securing end-user devices, such as laptops, smartphones, and desktops. These tools ensure that all devices accessing corporate resources comply with security policies and remain secure throughout their lifecycle.
Examples:
- Microsoft Intune: An endpoint management tool that helps manage devices, enforce security policies, and remotely deploy software, ensuring users have the right tools while keeping devices compliant.
- Jamf: Focuses on managing Apple devices, enabling secure setup, configuration, and software deployment across the enterprise.
>>> Read about endpoint management tools and understand how they ensure security and compliance
6. Security and threat protection tools
What is threat protection?
Threat protection tools help secure an organization by preventing unauthorized access, protecting against cyberattacks, and responding to threats in real time. These tools are crucial for safeguarding sensitive information and ensuring data security.
Examples:
- Microsoft Defender: Provides comprehensive threat protection, helping detect and mitigate potential security threats across endpoints and identities.
- CrowdStrike: A cloud-based threat protection tool that offers endpoint security, detecting threats, and taking necessary actions to protect against cyberattacks.
Microsoft 365 Solutions (Entra, Intune, Defender)

- Microsoft Entra: Provides identity and access management capabilities. Automatically assigns or revokes permissions during onboarding, promotions, and offboarding, supporting role-based access control to ensure secure and efficient access management.
- Microsoft Intune: Manages software deployment and device configurations. Automates software installation during onboarding or role changes, ensuring all required software is deployed efficiently. Also offers mobile device management (MDM) to control access from multiple devices.
- Microsoft Defender: Ensures endpoint security by providing protection against threats such as malware and ransomware. Helps monitor the security status of users' devices and respond to incidents quickly to keep user data secure.
>>> Read our comprehensive review of Microsoft Entra and see if it's right for you <<<
Okta
Official website: https://www.okta.com/
Offers Single Sign-On (SSO) and multi-factor authentication for secure access across multiple platforms.
- Simplifies user access during onboarding, promotions, and offboarding processes.
- Provides integration with hundreds of apps, making it easier to manage user identity.
SailPoint
- Automates user provisioning and access management.
- Ensures access aligns with user roles, reducing manual IT tasks.
- Provides visibility into user access to ensure compliance with policies.
JumpCloud

- Centralizes user access management in a cloud directory.
- Automates onboarding and offboarding processes.
- Provides group-based access control to simplify IT operations.
Splunk
- Monitors user activity in real time to detect unauthorized access.
- Provides detailed reports to help ensure compliance with security standards.
- Helps identify unusual patterns or anomalies in user behavior.
SolarWinds
- Tracks user access and activity, providing analytics for security compliance.
- Generates real-time alerts for unauthorized access attempts.
- Offers detailed audit logs for easy monitoring.
JAMF

- Specifically designed for managing Apple devices.
- Integrates with ULM to install, update, or uninstall software based on user roles.
- Simplifies IT management for Mac, iPhone, and iPad devices.
OneLogin
- Provides secure Single Sign-On for multiple business applications.
- Offers multi-factor authentication to enhance security.
- Allows easy management of user credentials, reducing IT workload.
Future trends in ULM
AI and Machine learning
- Behavior Analysis: AI can analyze user behavior patterns to predict needs, allowing proactive access adjustments.
- Adaptive Authentication: Machine learning can assess risks in real time and adjust authentication requirements accordingly.
Enhanced Data Security
- Advanced Encryption: New encryption techniques will help further protect user data, ensuring compliance with data protection standards.
- Continuous Compliance: Automated compliance checks ensure that user access adheres to evolving regulations, reducing manual effort.
Improved Employee experience
- Streamlined Onboarding: Future systems will focus on providing a seamless and user-friendly onboarding experience.
- Ongoing Engagement: Use analytics to keep users engaged, providing tailored resources and support throughout their lifecycle.
Conclusion
User Lifecycle Management (ULM) is vital for managing users from the moment they join to the moment they leave. By automating onboarding, promotions, and offboarding, ULM ensures users have the correct access at the right time, minimizing risks, improving productivity, and enhancing the overall user experience. Implementing a well-structured ULM system is key to a secure, efficient, and compliant workplace.
Struggling with onboarding delays? Consult Medha Cloud for a seamless User Lifecycle Management implementation. We provide the best possible solutions at the lowest cost with a quick turnaround
>>>> Talk to us – We’re available on Live Chat <<<<
Frequently Asked Questions
What is User Lifecycle Management (ULM)?
ULM is the process of managing a user's journey in a company, from joining to leaving. It includes setting up accounts, managing access, and removing access when no longer needed.
What are the main stages of ULM?
The main stages are onboarding (adding new users), role changes (updating access), and offboarding (removing access when users leave).
How can companies improve their ULM practices?
Companies can improve ULM by automating processes, personalizing user experiences, and regularly monitoring user activities to ensure everything is secure.
What tools can help with ULM?
Tools like Microsoft Entra, SailPoint, Splunk, and Okta can help automate and streamline ULM processes.
Bharath Kumar
Senior Microsoft 365 Consultant • 8+ years
Bharath is a Senior Microsoft 365 Consultant specializing in enterprise productivity solutions and white-label IT services. He has successfully deployed Microsoft 365 for over 200 organizations and helps MSPs build scalable white-label partnerships.
